- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have been looking at some old posts and thought to asked if there are any new workarounds for getting a public CA setup for remote configuration - intel AMT admin mode with a .local domain (with a DHCP option 15 that can't be changed.)
I thought to post this question to see if there are any other ways to get around this -
This is my current setup.
I have an EMA machine of "AMTcomputer@thedomain.local"
DHCP option 15 = thedomain.local
We have another domain as " anotherdomain@site.net.au"
So the obvious solution here is to change everything to " anotherdomain@site.net.au" including DHCP option 15 so the auto setup PKI could work.
Unfortunately, this isn't an option.
Any other ways to get an Intel AMT provisioning certificate for internal Domain name?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi S4m,
As Jose described for AMT Admin Control Mode you will have to meet general Intel AMT FW design requirements:
- Intel AMT Wired built in LAN + AMT Provisioning certificate issued by one of Intel AMT supported/trusted Public CAs -which for obvious reasons of DV process you can get for your publicly registered domain name + DHCP Option 15 set to value that will match domain name part of AMT provisioning cert CN.
OR - Add your own self signed CA Root cert hash to AMT FW so you can have cert CN domain name part matching any DHCP Option 15 you want. Note 1 - you still need ntel AMT Wired built in LAN
OR - set PKI DNS Suffix in Intel AMT FW to value of your publicly registered domain name. Once it is set it will make AMT FW to validate AMT Provisioning certificate domain name vs PKI DNS Suffix instead of network interface DHCP Option 15 and it will work for BOTH AMT Wired and Wireless networks as well.
With Intel EMA AMT configuration to ACM will even work over ANY network interface including non Intel AMT docks, USB-LAN dongles etc.
Note 2 - Intel AMT remote management access still requires Intel AMT enabled LAN, AMT WLAN or AMT LAN in TBT4 dock with Intel 11th Core vPro notebooks or newer (and vPro over TBT4 must be enabled by OEM in Intel ME FW in factory).
You can add your own CA root cert hash and /or set PKI DNS suffix (you can do both 2. and 3. above in one Pre-setup) via Intel MEBx manual interface or USB Pre-Provisioning which both require physical access and "touch" of each device.
OEM may do it for you in their factory but only for devices which are still in manufacturing mode and they usually charge approx $5-10 per device.
Fortunately there is pretty easy workaround for invalid internal domain names as long as your DHCP server is based on MS Windows service (or other solution that will support DHCP User classes and DHC Policies).
you need to ask DHCP Admin to:
-
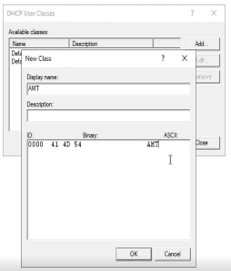
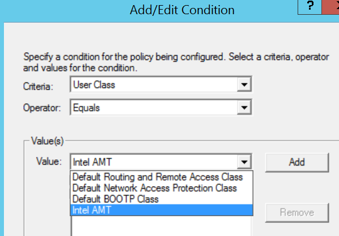
Create new User Class in DHCP server, Name it ex. AMT , you may also add description and Define its Class ID – ex. AMT
(enter Class ID name in ASCII column). -
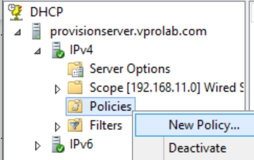
Define new DHCP Policy, name it ex. AMT, you may also add description, Add Condition for User Class = name you defined in New Class (select from the list), Add it
-
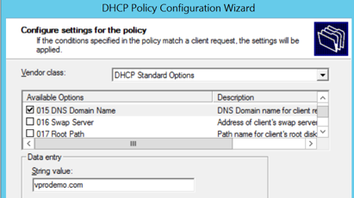
In DHCP Standard Options for this new Policy scroll down to Option 015 DNS Domain Name,
Select it and provide your company publicly registered domain name (ex. your site.net.au), Review settings and Finish
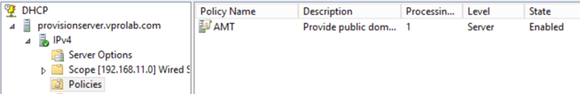
New Policy is added to DHCP server - then you have to deploy this new DHCP Policy for Intel AMT configuration time and purpose only:
in your EMAAgent.exe deployment script include in following order:
ipconfig /setclassid Ethernet AMT
where AMT shall be replaced by class ID you configured in first step. It will request from DHCP server to assign IP address within this New DHCP Policy with public domain name in Option 15.
EMAAgent.exe –fullinstall
TIMEOUT /T 180 /Nobreak
it will deploy EMAAgent which will register endpoint and start configuring Intel AMT automatically.
AMT configuration to ACM may take some time to complete so hence Timeout /T 180 /Nobreak command.
You may adjust time to be longer than those 3 min.
This is quick and not perfect example of giving Intel EMA time to complete AMT configuration to ACM mode.
other way is to query AMT configuration status to reach ACM with Intel® EMA Configuration Tool on 30-60 sec interval within script.
and than
ipconfig /setclassid Ethernet
which will revert back to default DHCP Policy (with your internal .local domain name in ?Option 15).
so your EMA Agent deployment script will look like:
ipconfig /setclassid Ethernet AMT
EMAAgent.exe –fullinstall
TIMEOUT /T 180 /Nobreakipconfig /setclassid Ethernet
Kudos to my team peer Josh Copeland for figuring out this "trick" - I am just sharing it
rgds
Dariusz Wittek
Biz Client Technical Sales Specialist | Intel EMEA CCG Technical Sales
Link Copied
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello S4m
Thank you for joining the community
Are you trying to migrate an existing installation without the need to purchase another provisioning cert? You don't need a provisioning cert if your systems are in Client Control Mode
Could you detail a bit more on your current setup?
Regards
Jose A.
Intel Customer Support Technician
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Jose,
Thanks for the response!
This is a new installation using Windows Authentication + Windows Server 2019. I have my own CA.
I've installed Intel EMA onto a VM "AMTcomputer@thedomain.local"
There is no migration as this is a new setup/prototype.
I am looking to get Admin mode to endpoints so I don't have to worry about user consent for advanced OOB functions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello S4m
It is certainly possible to use your own certificate but not that convenient as it requires to physically touch every remote system to "inject" your cert hash into the MEBx. The procedure is detailed in section 10.5.3: https://www.intel.com/content/dam/support/us/en/documents/software/Intel_SCS_User_Guide.pdf#page=222
Regards
Jose A.
Intel Customer Support Technician
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Jose,
With the amount of machines we have -- the overtime alone would be a nightmare!
I would prefer the auto setup.
Any suggestions?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello S4m
The autosetup will require a PKI certificate from 1 out of the 5 already included in the MEBx firmware. GoDaddy, Comodo, Entrust, Sectigo and DigiCert. Probably the amount of time saved will compensate the cost of the commercial certificate.
Regards
Jose A.
Intel Customer Support Technician
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Jose,
I am aware of the process of getting a public cert - but it is my domain name and DHCP DNS suffix which is causing me some greif.
As stated in the original post - my domain name has .local it it.
.local is a TLD that you simply can't get a cert for -- or domain name for that matter.
I wondering if you know any workarounds for this?
Perhaps this thread will help with understanding what I am after.
Prevent DHCP option 15 check (.local domain) - Intel Communities
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi S4m,
As Jose described for AMT Admin Control Mode you will have to meet general Intel AMT FW design requirements:
- Intel AMT Wired built in LAN + AMT Provisioning certificate issued by one of Intel AMT supported/trusted Public CAs -which for obvious reasons of DV process you can get for your publicly registered domain name + DHCP Option 15 set to value that will match domain name part of AMT provisioning cert CN.
OR - Add your own self signed CA Root cert hash to AMT FW so you can have cert CN domain name part matching any DHCP Option 15 you want. Note 1 - you still need ntel AMT Wired built in LAN
OR - set PKI DNS Suffix in Intel AMT FW to value of your publicly registered domain name. Once it is set it will make AMT FW to validate AMT Provisioning certificate domain name vs PKI DNS Suffix instead of network interface DHCP Option 15 and it will work for BOTH AMT Wired and Wireless networks as well.
With Intel EMA AMT configuration to ACM will even work over ANY network interface including non Intel AMT docks, USB-LAN dongles etc.
Note 2 - Intel AMT remote management access still requires Intel AMT enabled LAN, AMT WLAN or AMT LAN in TBT4 dock with Intel 11th Core vPro notebooks or newer (and vPro over TBT4 must be enabled by OEM in Intel ME FW in factory).
You can add your own CA root cert hash and /or set PKI DNS suffix (you can do both 2. and 3. above in one Pre-setup) via Intel MEBx manual interface or USB Pre-Provisioning which both require physical access and "touch" of each device.
OEM may do it for you in their factory but only for devices which are still in manufacturing mode and they usually charge approx $5-10 per device.
Fortunately there is pretty easy workaround for invalid internal domain names as long as your DHCP server is based on MS Windows service (or other solution that will support DHCP User classes and DHC Policies).
you need to ask DHCP Admin to:
-
Create new User Class in DHCP server, Name it ex. AMT , you may also add description and Define its Class ID – ex. AMT
(enter Class ID name in ASCII column). -
Define new DHCP Policy, name it ex. AMT, you may also add description, Add Condition for User Class = name you defined in New Class (select from the list), Add it
-
In DHCP Standard Options for this new Policy scroll down to Option 015 DNS Domain Name,
Select it and provide your company publicly registered domain name (ex. your site.net.au), Review settings and Finish
New Policy is added to DHCP server - then you have to deploy this new DHCP Policy for Intel AMT configuration time and purpose only:
in your EMAAgent.exe deployment script include in following order:
ipconfig /setclassid Ethernet AMT
where AMT shall be replaced by class ID you configured in first step. It will request from DHCP server to assign IP address within this New DHCP Policy with public domain name in Option 15.
EMAAgent.exe –fullinstall
TIMEOUT /T 180 /Nobreak
it will deploy EMAAgent which will register endpoint and start configuring Intel AMT automatically.
AMT configuration to ACM may take some time to complete so hence Timeout /T 180 /Nobreak command.
You may adjust time to be longer than those 3 min.
This is quick and not perfect example of giving Intel EMA time to complete AMT configuration to ACM mode.
other way is to query AMT configuration status to reach ACM with Intel® EMA Configuration Tool on 30-60 sec interval within script.
and than
ipconfig /setclassid Ethernet
which will revert back to default DHCP Policy (with your internal .local domain name in ?Option 15).
so your EMA Agent deployment script will look like:
ipconfig /setclassid Ethernet AMT
EMAAgent.exe –fullinstall
TIMEOUT /T 180 /Nobreakipconfig /setclassid Ethernet
Kudos to my team peer Josh Copeland for figuring out this "trick" - I am just sharing it
rgds
Dariusz Wittek
Biz Client Technical Sales Specialist | Intel EMEA CCG Technical Sales
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Mr_vPro,
Thank you (& to Josh) for this detailed post - exactly what I am after.
This looks like it will work for my set up - great info!
Once I start the works I will report the outcome.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello S4m
Thank you for the clarification. Let me try to research on this. I will get back to you soon.
Regards
Jose A.
Intel Customer Support Technician
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello S4m
After consulting with our senior team we got the following: The short answer is no. Not if you want to use .local as your domain. You must use a domain that is recognized by AMT for an ACM provisioning cert. This is true even if you set up a self-sign CA server. You want to take a look at: Intel® AMT SDK Implementation and Reference Guide
Regards
Jose A.
Intel Customer Support Technician
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello S4m
I am just following up to double-check if you found the provided information useful. If you have further questions please don't hesitate to ask. If you consider the issue to be completed please let us know so we can proceed to mark this ticket as resolved. I will try to reach you as a very last time on next Thursday 21th. After that the thread will be automatically archived.
Regards
Jose A.
Intel Customer Support Technician
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Jose,
Thanks for the information.
I'm wondering if you can elaborate on this comment from this thread?
https://community.intel.com/t5/Intel-vPro-Platform/Prevent-DHCP-option-15-check-local-domain/m-p/431258
"Spoofing of DHCP or additional Reservations only for the process of initial AMT configuration"
Can you please explain what is happening here?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello S4m
Well, that particular comment was written by the community user JWint3, which makes it difficult to guess exactly what we meant. What we know is that option 15 is not available on latest versions of AMT, unfortunately.
Regards
Jose A.
Intel Customer Support Technician
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm having a similar problem. Anyone can look at the issue on my post?
AMT not provisioning as ACM - Intel Communities
Not sure why it got blacklisted, i may not be able to post new threads since I'm a new member.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page