- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please note that with 12th Gen Intel vPro® Enterprise (AMT) & Essentials (ISM) platforms and with 11th Gen Intel vPro® (AMT) Desktop platforms your AMT TLS-PKI provisioning certificate with SHA1 Root certificate will not allow you to provision Intel AMT/ISM, even if Root CA cert hash is still embedded in ME FW.
With Intel ME FW 11.0.x and newer Intel ME FW does not accept SHA1 AMT Provisioning leaf certificates neither intermediate certificates with SHA1 algorithm.
But SHA1 Root certificates were accepted by Intel ME FW so PKI-TLS provisioning process worked.
With Intel ME FW 16.x (all platform types) and ME FW 15.x H - Desktop platforms Intel ME FW support for SHA1 Root certificates was deprecated, so AMT provisioning certificate with SHA1 Root cert trust chain does not work anymore (while working fine for older ME FW).
This issue is pretty confusing as Intel ME FW still contains SHA1 Root certificates hashes embedded and ME FW 15.x laptops being configured correctly while same generation desktops fail to get configured.
Please see complete list of Intel ME FW factory default embedded certificate hashes list:
https://software.intel.com/sites/manageability/AMT_Implementation_and_Reference_Guide/default.htm?turl=WordDocuments%2Frootcertificatehashes.htm
For most of those CAs there is SHA2 version of their Root cert embeded in Intel ME FW, so all you have to do it to ask to reissue (depending on CA it may be or not free of additional charge) your current certificate with complete SHA2 only trust chain instead of mixed SHA1-SHSA2 trust chain.
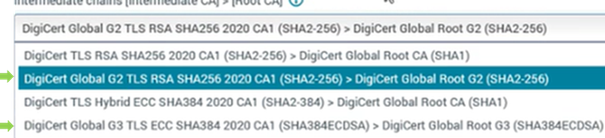
You shall use issuing CA selection feature -for example Digicert allows you to pick trust chain :
you shall select one of those marked with green arrow.
Other CAs may have complete SHA2 selected as default (so selection may not be even exposed /made available).
For example for GlobalSign all their public Root cerificates are SHA2 so nothing to bother about.
If you are using AMT provisioning certificate issues by Sectigo with old Comodo/Sectigo AAA Root it is SHA1 Root cert and will fail in above scenarios.
If you use older ME FW 10.x -14.x unfortunately you will have to use another Issuing CA and purchase new AMT Provisioning certificate with complete SHA2 trust chain.
As you may see in above link, in Intel ME FW 15.0.45, 16.1.x new Sectigo User Trust SHA2 Root was added.
So you may purchase and use second AMT provisioning certificate for ME FW 15.0.45 and 16.1 (nor earlier than those).
Second AMT Provisioning certificate may be used with Intel EMA Only (Intel SCS is EOL'ed and will pick first matching certificate form RCS Service cert store, which will be old SHA1 Sectigo AAA Root issued one).
In addition, releases supporting this root certificate are planned for Intel® ME FW 12 and 14.
I will update this post once those builds of ME FW 12/14 will be launched.
rgds
Dariusz Wittek
Biz Client Technical Sales Specialist | Intel EMEA CCG Technical Sales
Intel Corporation | intel.com
Link Copied
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page