- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dear Intel Employers,
I have question about microcodes and possibly vulnerability at Intel Core 2 Duo T7300. This CPU have fews bugs: spectre_v1, spectre_v2, srbds, tsx_async_abort, itlb_multihit, l1tf, mds, meltdown, spec_store_bypass.
I found on this site link to github: https://software.intel.com/security-software-guidance/processors-affected-transient-execution-attack-mitigation-product-cpu-model
Github: https://github.com/intel/Intel-Linux-Processor-Microcode-Data-Files/tree/master/intel-ucode
I have some questions:
- First these microcodes are from Intel ?
- Second these microcodes should fix all vulnerbalities for Intel Core 2 Duo T7300?
- Third I have some problems with microcode. I found something but I don't want write it public so I want to contact with Intel employer and talking about it. Maybe they can fix it.
- Fourth is it option to install new microcode to BIOS if device is end of life and manufacturer will not make new BIOS version?
I hope that people from Intel will read this.
Thanks for reading my post. I wish good day for all!
Link Copied
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Piotr,
Thank you for posting on the Intel® communities.
Due to this product being discontinued, I need to inform you that Intel Customer Service no longer supports inquiries for this product, but perhaps fellow community members have the knowledge to jump in and help.
You may also find the Discontinued Products website helpful to address your request.
https://www.intel.com/content/www/us/en/support/discontinued-products.html
Please keep in mind that this thread will no longer be monitored by Intel.
Regards,
Esteban D.
Intel Technical Support Technician
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I will also point out that it was decided that Intel would NOT provide any microcode updates for processors this old (14 years). Some of these vulnerabilities are mitigated by changes made in the O/S -- but note I am talking about Windows 10, not the versions of Windows available 14 years ago. Similar mitigations were added to the linux O/S, but I do not know if they are actually applied for processors this old.
...S
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you very much for answer. I know that this CPU is old. On this website I can't find any information about T7300 - https://www.intel.com/content/www/us/en/support/discontinued-products.html
I don't know if I undestand your answer correctly because my english is poor. This product is discountinued and you decided that you will not update microcodes in the future. Okay it is easy to understand but you don't answer when you last updated microcode for this CPU (T7300). I must know what vulnerabilities should be fixed because maybe this can be problem with OS so maybe people can fix it. What vulnerabilities was fixed by Intel (microcode)? Can you tell me?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
All I can tell you is that, at the time when the Spectre and Meltdown vulnerabilities were first being mitigated, the decision was made to NOT do anything regarding long-discontinued processors such as yours. Similarly, nothing has (or is) being done regarding any of the subsequently identified vulnerabilities.
Saying this another way, there are no microcode updates for your processor that close any of these vulnerabilities. You have some mitigations that were introduced at the O/S level but that's it. As for what mitigations are included in any particular O/S or O/S release, well, you need to be talking to the people that are responsible for these O/S releases; I don't have the time, nor the interest, in enumerating them for you.
There is a lot of information available in the intel Security Center (https://www.intel.com/content/www/us/en/security-center/default.html); feel free to start there.
...S
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for your information. I am suprised that Intel doesn't fix some security issues for this CPU.
I did research and I am followed this information from your website: "Linux Users: The microcode image is named after the family/model/stepping. You can locate these from /proc/cpuinfo. Example: For Family 06, Model 85, Stepping 4 (values in decimal), the corresponding microcode file is 06-55-04 located in /lib/firmware/intel-ucode/ (values in hexadecimal)."
I did the same for my CPU and I can find that on your github website are file with my microcode: https://github.com/intel/Intel-Linux-Processor-Microcode-Data-Files/tree/master/intel-ucode
You told me that you doesn't update microcode for T7300 but information on the up is opposite to your information so I don't know maybe I am wrong and I did this not correctly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The /proc/cpuinfo output is in decimal, but the microcode file names are in hexadecimal. You've probably forgotten to do the conversion. What are the family, model, stepping of your processor according to /proc/cpuinfo?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
"The /proc/cpuinfo output is in decimal, but the microcode file names are in hexadecimal. You've probably forgotten to do the conversion. What are the family, model, stepping of your processor according to /proc/cpuinfo?"
I know that in /proc/cpuinfo is in decimal. I found my microcode but this microcode doesn't fix all vulnerabilities on the system. This is my microcode: https://github.com/intel/Intel-Linux-Processor-Microcode-Data-Files/blob/master/intel-ucode/06-0f-0b
Can you tell me what vulnerabilities this fix? All of them or maybe part?
It is a pity that Intel leaves old devices. I am poor guy and I don't have money to new system. In the future probably I will choose AMD because they doesn't have a lot of vulnerabilities.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I didn't say that you won't find microcode updates for your processor; I said that you won't find any mitigations for any of the vulnerabilities within the microcode for your processor.
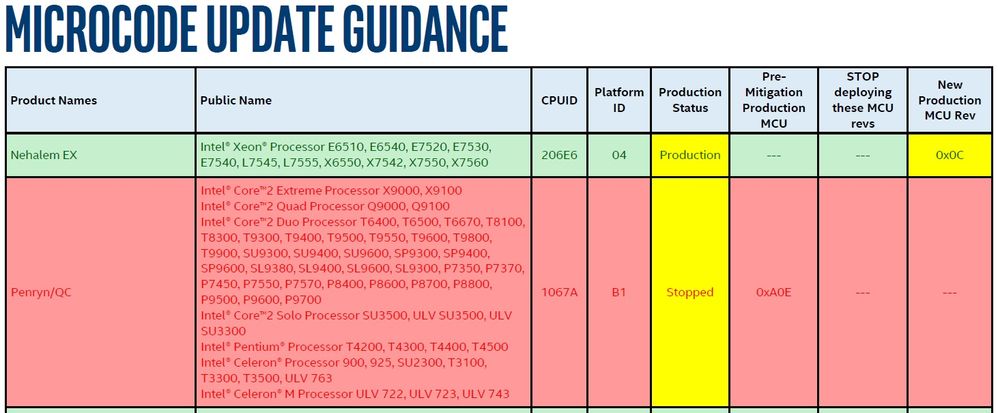
Your processor family (Merom) is so old it isn't even mentioned in Intel's update guidance. The successor to Merom, Penryn is mentioned, however:
What does "Stopped" mean? It means nothing is being done:
...S
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page