- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
During scanning our Windows computers for a possible OpenSSL vulnerability known as CVE-2022-3602 or CVE-2022-3786, we encountered that the Intel(R) System Usage Report Service is using OpenSSL 3.0.2. This version of OpenSSL is vulnerable and is mainly found in the file C:\Program Files\Intel\SUR\QUEENCREEK\x64\libcrypto-3-x64.dll
Is this a known issue at Intels and has a fix already been released?
If so, please inform me Intels statement about this vulnerability and how to fix this (if necessary).
If not, can we disable this Windows service in the meantime without any issues?
Regards,
Jasper Kimmel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello JasperKimmel,
Thanks for your patience. Based on the investigation, this issue seems related to the Intel® Computing Improvement Program (Intel® CIP).
As a test, please uninstall the tool and let me know if the issue persists.
Steps: locate the Intel® Computing Improvement Program (Intel® CIP) in the Control Panel -> Programs and uninstall it. Uninstalling will remove the .exe files and DLL's and the Intel CIP service should not run anymore, stopping the error messages.
Also, I recommend you report the vulnerability by following this article:
- How Do I Report Security and Vulnerability Issues Related to Intel® Products?: https://www.intel.com/content/www/us/en/support/articles/000056781/programs/intel-corporation.html
@splendidprofessional, @chris-jnctn, @sharkie, I recommend you follow these steps or open a new thread so you all can get proper support.
Best regards,
Deivid A.
Intel Customer Support Technician
Link Copied
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello JasperKimmel,
Thank you for posting on the Intel® communities. I am sorry to know that you are having issues related to a vulnerability.
In order to better assist you, please provide the following:
1. What is the brand and model name of your processor?
2. What is the brand and model name of your motherboard (if desktop) or laptop and its BIOS version?
3. What is the Windows version and build?
Regards,
Deivid A.
Intel Customer Support Technician
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @DeividA_Intel,
I have a Microsoft Surface with Intel components (see attached image for the details of my system). I installed the Intel Driver Support Assistant (IDSA) and use this to keep my Intel drivers and components up to date. The vulnerable DLL is either part of the IDSA or part of one of the Intel drivers.
Regards,
Jasper Kimmel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
During scanning our Windows computers for a possible OpenSSL vulnerability known as CVE-2022-3602 or CVE-2022-3786, we encountered that the Intel(R) System Usage Report Service is using OpenSSL 3.0.2. This version of OpenSSL is vulnerable and is mainly found in the file C:\Program Files\Intel\SUR\QUEENCREEK\x64\libcrypto-3-x64.dll
Is this a known issue at Intels and has a fix already been released?
If so, please inform me Intels statement about this vulnerability and how to fix this (if necessary).
1. What is the brand and model name of your processor?
Intel(R) Core(TM) i5-1035G7 CPU @ 1.20Ghz
2. What is the brand and model name of your motherboard (if desktop) or laptop and its BIOS version?
Microsoft motherboard.
3. What is the Windows version and build?
windows 10 enterprise edition (x64)
10.0.19044
19044.1806
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @splendidprofessional ,
Thanks for your response, however, I would like to know if you are facing the same issue as JasperKimmel or if you are replying in behave of JasperKimmel.
@JasperKimmel, please let me know if you are working with splendidprofessional to make sure that I can proceed with the info provided by splendidprofessional or if we have the same issue but with different users.
I am sorry for the inconvenience.
Regards,
Deivid A.
Intel Customer Support Technician
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @DeividA_Intel ,
@splendidprofessional is facing the same issue because I'm not familiar with this person.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
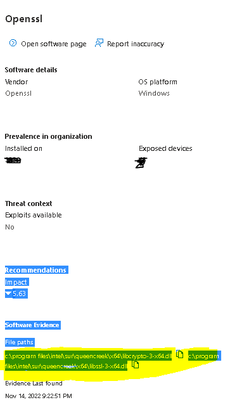
Hi I'm having the same issue, Microsoft 365 Defender is reporting the same issue. See the attached screenshot.
1. What is the brand and model name of your processor?
Intel(R) Core(TM) i5-10210U CPU @ 1.60GHz
2. What is the brand and model name of your motherboard (if desktop) or laptop and its BIOS version?
Model NUC10i5FNH, Bios FNCML357.0058.2022.0720.1011
3. What is the Windows version and build?
Microsoft Windows 10 Enterprise - 10.0.19045
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
I've allows seen this issue,
Nothing to do with Motherboard or bios or Processor
issue is the Driver software is using OpenSSL and
So, Intel WHEN you are going to update your Driver software to patch this issue ?
see below
Executive summary
On October 25, 2022, OpenSSL announced the release of OpenSSL version 3.0.7, which will address a critical security issue. OpenSSL version 3.0.7 became generally available on November 1st 2022. The security issue has since been downgraded from a Critical rating to a High severity rating.
The vulnerability is a denial-of-service for systems that support client certificate-based authentication. An attacker could send a maliciously crafted certificate to a server that parses certificates as part of client authentication and crash the server. At the time of this report, the vulnerability does not appear to allow Remote Code Execution (RCE), however OpenSSL states in their advisory that since their codebase is distributed as source code, some product implementations might have implemented the code in such a way that RCE could be triggered on some platforms. However they do state that exposure to remote code execution is not expected on any platforms.
The only known mitigation at the time of this report is to upgrade to OpenSSL version 3.0.7. Customers can track their exposure and patching status once the patch and CVE are released using Microsoft Defender Vulnerability Management, by navigating to the Endpoints Exposure tab of the report.
For more information about impacted Microsoft products, please see the following MSRC blog.
Analysis
The denial-of-service (DoS) vulnerability stems from a buffer overflow which can be triggered in name constraint checking when OpenSSL does X.509 certificate validation. The buffer overflow occurs after certificate chain validation and require a Certificate Authority to sign a malicious certificate, – which is not unlikely – or for an application to continue certificate validation, despite failing to construct a certificate chain to a trusted issuer.
Attackers exploit the vulnerability by crafting a malicious email address containing the '.' character in the X.509 certificate to cause an overflow of an arbitrary number of bytes. This could result in a crash and cause a Denial of Service.
This impacts both TLS clients and servers. For a client, the vulnerability could be triggered by connecting to a malicious server. For a server, it can be triggered if the server requests client certificate authentication and a client with a maliciously configured certificate connects to the server.
Mitigation
Apply the following mitigation to reduce the impact of this threat. Check the recommendations card for the deployment status of monitored mitigations.
Upgrade to OpenSSL version 3.0.7 as soon as it is available
Reference
Attack Surface: CVE-2022-3602 - OpenSSL 3 Buffer Overflow on Certificate Validation of Email Address . Microsoft Defender Threat Intelligence (accessed 11-01-2022)
CVE-2022-3786 and CVE-2022-3602: X.509 Email Address Buffer Overflows. OpenSSL.org (accessed 11-01-2022)
OpenSSL version 3.0.7 published. OpenSSL.org (accessed 11-01-2022)
https://www.openssl.org/news/secadv/20221101.txt. OpenSSL.org (accessed 11-01-2022)
Forthcoming OpenSSL Releases. OpenSSL.org (accessed 10-31-2022)
Change log
2022-11-01 16:55 UTC | Updated vulnerability details
2022-10-31 19:00 UTC | Entry created
Copyright
© Microsoft 2022. All rights reserved. Reproduction or distribution of the content of this site, or any part thereof, without written permission of Microsoft is prohibited.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I agree with @sharkie on this. It has nothing to do with hardware. Instead, it has anything to do with software provided by Intel. The only reason why I posted my message in the processor support forum is that there is no support forum related to software.
@DeividA_Intel: Please escalate this issue to your security team and urge them to update this particular driver or tool?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello JasperKimmel,
Thanks, JasperKimmel and everyone for the information provided.
I will proceed to check the issue internally and post back soon with more details.
Best regards,
Deivid A.
Intel Customer Support Technician
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello JasperKimmel,
Thanks for your patience. Based on the investigation, this issue seems related to the Intel® Computing Improvement Program (Intel® CIP).
As a test, please uninstall the tool and let me know if the issue persists.
Steps: locate the Intel® Computing Improvement Program (Intel® CIP) in the Control Panel -> Programs and uninstall it. Uninstalling will remove the .exe files and DLL's and the Intel CIP service should not run anymore, stopping the error messages.
Also, I recommend you report the vulnerability by following this article:
- How Do I Report Security and Vulnerability Issues Related to Intel® Products?: https://www.intel.com/content/www/us/en/support/articles/000056781/programs/intel-corporation.html
@splendidprofessional, @chris-jnctn, @sharkie, I recommend you follow these steps or open a new thread so you all can get proper support.
Best regards,
Deivid A.
Intel Customer Support Technician
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks @DeividA_Intel . I removed the software and the vulnerability was not found anymore. I also dropped a mail to Intels Security Center.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello JasperKimmel,
Thanks for the confirmation. I am glad to know that the issue is no longer present after you uninstall the Intel® Computing Improvement Program (Intel® CIP).
Since the issue was solved, I will proceed to close this thread. However, you can open a new one in case you need further support or if you encounter any future issues.
Regards,
Deivid A.
Intel Customer Support Technician
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page