- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Intel SGX provides paging functionality. Therefore, when a large amount of EPCs are allocated, the pages are evicted to the Untrust area. My question is, when using a certain amount of Enclave, is it possibly to evict EPCs by using a large amount of memory in the Untrust area? Also, is it possibly that when a large amount of memory is used in the Untrust area, if we try to allocate a large Enclave, a small number of EPCs will be allocated due to the memory in the Untrust area?
I would appreciate it if you could help me out.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Thank you for your interest in Intel® SGX.
I am checking if the large amount of memory used will result in any differences in the EPC allocated memory. I will get back to you if I have more information for this.
In the meantime, Intel® SGX uses Enclave Page Cache (EPC) to store enclave contents. When the enclaves are larger than the total memory available to the EPC, enclave paging are used by privileged SW to evict some pages to swap in other pages.
This process has an inherent overhead associated with it, the more pages are swapped out, the more often the overhead is incurred.
For large enclave, it is suggested to include only secrets and code to operate on them in the enclaves. This is to ensure the enclave size is less than the EPC, and minimize the chances of incurring paging overhead.
Regards,
Ken
Link Copied
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Thank you for your interest in Intel® SGX.
I am checking if the large amount of memory used will result in any differences in the EPC allocated memory. I will get back to you if I have more information for this.
In the meantime, Intel® SGX uses Enclave Page Cache (EPC) to store enclave contents. When the enclaves are larger than the total memory available to the EPC, enclave paging are used by privileged SW to evict some pages to swap in other pages.
This process has an inherent overhead associated with it, the more pages are swapped out, the more often the overhead is incurred.
For large enclave, it is suggested to include only secrets and code to operate on them in the enclaves. This is to ensure the enclave size is less than the EPC, and minimize the chances of incurring paging overhead.
Regards,
Ken
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Thank you for reply!
We look forward to your answer.
Best regards
wwfbear789
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi wwfbear789,
Thank you for your patience.
This information might be related to your question.
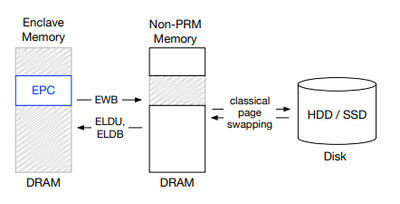
SGX offers an EPC page eviction method that can defend against a malicious OS that attempts any active address translation attacks. Enclaves do not trust the system software in the SGX threat model.
SGX supports evicting EPC pages to DRAM pages outside the PRM range. The system software is expected to use its existing page swapping implementation to evict the contents of these pages out of DRAM and onto a disk as shown in the figure.
If the EPC page is evicted , any attempt to access the page from the enclave code will result in Page Fault. Therefore, OS kernel's page handler needs to be able to extract the virtual page number in order to load back the page into the DRAM.
Refer to Intel SGX Explained Section 5.5 (Page 69) for more information regards to EPC page Eviction.
Hope this is helpful, please let me know if you have questions.
Regards,
Ken
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page