- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
while provisioning endpoint with TLS-PKI we get an error - AUTH_FAILED. The endpoint has static IP adress on management interface and manualy assigned DNS-suffix unicomm.com.ua. FQDN of EMA server is ema.unicomm.com.ua.
ME version is v16.1.30.2269
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Intel AMT is designed to work perfectly fine in isolated corporate networks as well. The only misleading /confusing element is requirement to use selected Public CA as issuer of AMT Provisioning cert due to fact that those supported Root CA cert hashes are pre embedded in ME FW Root cert list and by design those CA will not support certificate CN's in invalid domain names (not registerable in Public DNS).
So far you handled it.
For lack of DHCP you may consider setting up small DHCP server in the network just for Intel AMT provisioning process needs. If its Option 15 will be set to your public DNS domain name (please also note Extended Top Level Domain support as per PKI verification link in one of my replies - for .ua check level depth is 2) and AMT provisioning will be done over Intel AMT build in Wired LAN - you will not have to set PKI DNS suffix.
Once Intel EMA will provision and configure Intel AMT to use Static IP it will not use DHCP server anymore until you unconfigure it again so small IP addresses scope shall cover AMT onboarding process.
Intel AMT CIRA MTLS connection is the most secure mode of AMT communication and there is nothing what may stop using it also in intranet network.
Setting Intel AMT to Static IP has one side effect - with no DHCP used for Intel AMT Environment Detection Intel AMT will use both CIRA MTLS outgoing tunnel to Intel EMA and also will listen for Intel AMT incoming traffic on AMT TCP ports.
rgds
darek
Link Copied
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello ssh911,
Thank you for contacting Intel Support for your case.
I would like to know if this is a new config or if this was working before. Also please provide information about the certificate being used, if it is self made or purchased.
Please provide pictures from each tab of the certificate accesing it through ISS.
Please indiate what are the EMA, OS, SQL version and where each are located.
Lastly, please indicate if you tried with Client Control mode, if you have an static IP and endpoints and server are within the same LAN.
I will monitor your case today and follow up tomorrow if needed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dear Eduardo_B_Intel
Thank you for your reply.
Please find information about certificate and server logs attached.
Some requested info about our environment:
- new installation
- EMA version 1.12.2.0
- OS Windows Server 2022 Evaluation
- SQL Server 2022 Express
- both endpoint and server configured with static IP but in different routed LAN IP segments (10.2.1.0/24 - endpoint network, 10.3.1.4/24 - EMA server).
- Host-based provisioning in CCM works.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
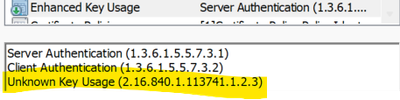
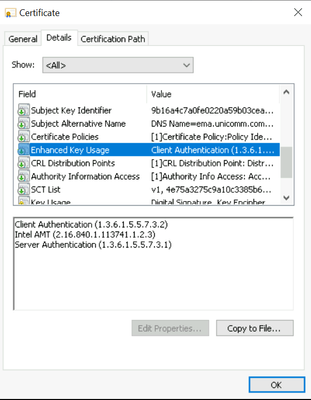
Please verify that your AMT Provisioning certificate (issued by DigiCert) has Intel AMT unique OID (2.16.840.1.113741.1.2.3) in Extended Key Usage (EKU) field ?
If it doesn't it will not be accepted as valid AMT provisioning cert by Intel ME FW so even if cert chain is complete and you (EMA) has private key for this cert it is not good for CCM to ACM change authorization.
See more details on process/requirements https://software.intel.com/sites/manageability/AMT_Implementation_and_Reference_Guide/default.htm?turl=WordDocuments%2Fpkicertificateverificationmethods.htm
You need to follow following guide for cert ordering How to Purchase and Install DigiCert*, Entrust* and/or GoDaddy*... (intel.com) -check DigiCert document - page 11(13) "check the box for vPro “Include the Intel vPro EKU(Extended Key Usage) field in the certificate."
Check with Digicert for options to revoke current cert and reissue new one with same CN and validity date without additional cost.
Once you receive new cert - renew it in any cert store and then export as complete trust chain certs (3 certs) with private key into .pfx file.
Last -remove current one (without AMT OID) from EMA certificates (via EMA WebUI) and import new one.
rgds
Dariusz Wittek
Biz Client Technical Sales Specialist | Intel EMEA CCG Technical Sales
PS. and let us know if it helped
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, this certificate marked in EMA web interface as "TLS-PKI" and was issued with Intel vPro EKU option.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi.
Can you provide more details on "DNS-suffix unicomm.com.ua. FQDN of EMA server is ema.unicomm.com.ua"
Have you set PKI DNS Suffix in Remote Configuration section in MEBx ? or ... domain name suffix in AMT LAN Static IP only (this one does not work for ACM mode).
Did you also set provisioning server FQDN in same section as PKI DNS Suffix? it sets strict check of complete AMT Provisioning cert CN vs this value - it seems to be matching in your case but if strict check (instead of just CN domain name part check vs PKI DNS Suffix) which may sometimes cause issues if full match can't be assured.
One more thing - you shall import AMT provisioning cert into EMA as one record (complete trust chain) -once imported you shall see all 3 certs (sometimes 4) being imported together: AMT provisioning leaf cert, issuing CA cert, (internediate CA) and Root CA cert.
Intel EMA does not rebuild cert trust chain from any cert store itself, instead it is using cert trust chain from EMA DB record.
rgds
darek
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I did not change any settings in MEBx, it full unprovisioned. At endpoint's OS (Windows 10 LTSC) I have configured static IP address on LM network adapter and set DNS-suffix as unicomm.com.ua. To provison I am using EMA_agent with coresponding agent policy file, both downloaded from EMA portal.
The EMA server has hostname ema.unicomm.com.ua (as CN in certificate)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, do you mean you set (Primary) DNS suffix in OS?
it does not matter/help with Intel AMT, and it explains root cause of your failure.
Please review https://software.intel.com/sites/manageability/AMT_Implementation_and_Reference_Guide/default.htm?turl=WordDocuments%2Fpkicertificateverificationmethods.htm
again.
AMT certificate is verified vs :
its trust chain to anchor one of AMT FW embedded Root CA cert hashes and being AMT Provisioning cert (AMT OID in EKU) you have it OK.
Plus
Intel AMT Wired LAN (i219LM) connection-specific DNS Suffix (it is assigned by DHCP server option 15)
or
ME FW PKI DNS Suffix as defined in Intel MEBx interface. PKI DNS suffix allows AMT configuration into Admin Control mode also over WiFi and any other network interface (AMT manageability works only over Intel AMT LAN/WLAN/AMT capable TBT Docks (if supported by OEM 11th Gen Core vPro platform and newer).
if you have DHCP server in your network please set its Option 15 to your AMT cert CN domain name part (unicomm.com.ua). If Option 15 is already set and can't be changed for other reasons/use see my other post https://community.intel.com/t5/Intel-vPro-Platform/Intel-AMT-Provisioning-Certificate-with-a-local-domain/m-p/1397682
OR (especially if there is no DHCP server in your static IP network) set PKI DNS Suffix to your AMT cert CN domain name part (unicomm.com.ua) in Intel MEBx (during POST reboot).
Please also remember to set IP address to "Use a static IP" in EMA AMT Profile settings:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for reply.
It is closed private network of industrial pc's without DHCP and Internet access. I'll try your last solution tomorrow and give you feedback.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Intel AMT is designed to work perfectly fine in isolated corporate networks as well. The only misleading /confusing element is requirement to use selected Public CA as issuer of AMT Provisioning cert due to fact that those supported Root CA cert hashes are pre embedded in ME FW Root cert list and by design those CA will not support certificate CN's in invalid domain names (not registerable in Public DNS).
So far you handled it.
For lack of DHCP you may consider setting up small DHCP server in the network just for Intel AMT provisioning process needs. If its Option 15 will be set to your public DNS domain name (please also note Extended Top Level Domain support as per PKI verification link in one of my replies - for .ua check level depth is 2) and AMT provisioning will be done over Intel AMT build in Wired LAN - you will not have to set PKI DNS suffix.
Once Intel EMA will provision and configure Intel AMT to use Static IP it will not use DHCP server anymore until you unconfigure it again so small IP addresses scope shall cover AMT onboarding process.
Intel AMT CIRA MTLS connection is the most secure mode of AMT communication and there is nothing what may stop using it also in intranet network.
Setting Intel AMT to Static IP has one side effect - with no DHCP used for Intel AMT Environment Detection Intel AMT will use both CIRA MTLS outgoing tunnel to Intel EMA and also will listen for Intel AMT incoming traffic on AMT TCP ports.
rgds
darek
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Setting PKI DNS suffix to unicomm.com.ua solves the problem and now provisioning in ACM fully works.
Thank you very much for your help!
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page