Cohesity recently announced a new collaboration with Intel to bring confidential computing technology to Cohesity Data Cloud. Using Intel® Software Guard Extensions (Intel® SGX) and Intel® Trust Authority, Cohesity enables hardware-enabled security that helps protect customer backup data from enterprise databases, NAS environments, SaaS apps, virtual machines, and cloud environments.
Where traditional security has focused on data in transit and data at rest – both essential tactics – data in memory has remained relatively vulnerable. Intel SGX helps solve this by creating a Trusted Execution Environment (TEE) designed to keep secrets in encrypted memory using processor-controlled keys. Cohesity is bringing this technology to the data security and management space to give customers additional protection and mitigation.
The Status Quo
For many years, information security often consisted of simply keeping network traffic within an organization's network, perhaps with firewalls and other perimeter defenses. As more traffic traveled over the internet, and as more organizations realized that malicious actors could exist within their own networks, the industry moved to encrypting all network traffic (e.g., data-in-motion). Cohesity, for example, supports industry-standard encryption protocols to protect your data while it’s being backed up to a Cohesity cluster.
While protecting data in motion is necessary, it isn’t sufficient. A bad actor can still hack into a system and copy the data or simply walk off with your hard drives. To help combat this, Cohesity provides the ability to encrypt your data before it’s stored on disk. This ensures that an attacker who obtains a copy of the drive still can’t read your data.
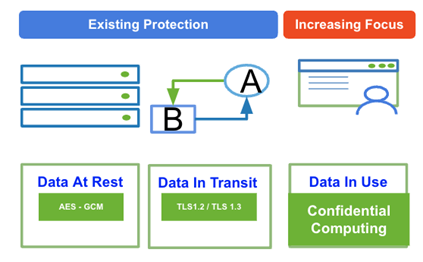
Encrypting data-at-rest and data-in-motion are obviously immense wins for security, but it’s still not perfect. There’s still one weak link – memory.
The problem with memory is fairly simple and has plagued the software industry for decades. To encrypt data, an encryption key must be available to the processor. Since processors, by necessity, need to keep the data they’re working on in memory, that means an attacker with access to a system’s memory can potentially extract the encryption keys and use them to decrypt the encrypted data. This is the essence of HeartBleed and other memory leak attacks. Clever researchers have even been known to resort to dunking RAM chips in liquid nitrogen to preserve data in the chips long enough to extract the secrets. The rise of cloud computing has brought memory disclosure attacks to the forefront because organizations may be sharing physical machines with other organizations. This is further complicated by the relatively large number of people with access to these systems: your organization, your cloud service provider, and the cloud infrastructure provider.
A prudent organization then will seek to protect their data while “in use” (e.g. in RAM) as well as in transit and at rest. This is where Cohesity and Intel’s collaboration comes in.
Cohesity Data Cloud and Intel Confidential Computing
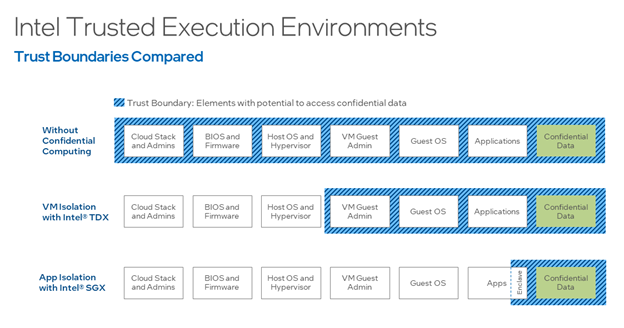
Cohesity uses Intel SGX to keep secrets confidential, even from root users on the system. With Intel SGX, only the code or functions inside the protected enclave are granted access to confidential data. Other software in the virtual machine, cloud tenants, the cloud stack, and admins are not allowed access. Creating a TEE causes the processor to associate a region of memory with a specific application and keep that memory encrypted at all times. If that data is needed, it is only decrypted within the processor itself, where it is much less vulnerable.
Cohesity uses TEEs to protect secondary data stored on Cohesity Data Cloud. These TEEs handle the keys used to encrypt or decrypt stored backups. By doing so, Intel and Cohesity address the problem of needing unencrypted keys in memory to perform cryptographic operations. Instead, memory is encrypted with keys that only the processor knows. An attacker can’t read a secret from memory if the secret isn’t there.
As shown in this diagram, confidential computing helps Cohesity reduce the attack surface to only the processor and function that is running in the TEE, rather than the entire system.
Still, you’re trusting that small program that handles encryption along with the processor itself. What if said program is no longer trustworthy because an attacker has corrupted it? How do you know that the TEE is a real one, is patched correctly, and is running the up to date firmware? How do you know that the program is exactly what is expected to run? This is where Intel Trust Authority comes in. Intel Trust Authority uses cryptographic keys embedded in the processor itself, and digital signatures on the program associated with a TEE to validate that the environment runs only a genuine Intel processor in a secure mode executing an application approved for use with that TEE. Since the application is signed by the developer, validated by the processor, and assigned to a specific TEE, an attacker who alters the application won’t have access to the TEE containing your secrets.
By combining Intel Trust Authority and Intel SGX, Cohesity helps organizations improve their security posture and reduce their risk even further. You can now sleep a little better at night knowing that your data remains encrypted while in transit, at rest, and now in use.
Learn more about Cohesity Data Cloud and Intel confidential computing solutions.
 Raghu Yeluri is an Intel Fellow and Lead Security Architect for Confidential AI and Confidential Computing Services in Intel’s Office of the CTO. He is the chief architect of Intel Trust Authority, Industry's first operator independent multi-cloud attestation service for multi-vendor TEEs and confidential workloads, released in 2023. Over the last decade, he has successfully architected multiple solutions for 'trusted computing' that are broadly deployed in many private and public cloud environments. He is a frequent presenter at technical conferences like Kubecon, OC3, Intel Innovation, IBM Think, VMWorld, etc. on Security. Raghu has 10+ patents in security, attestation, confidentiality/integrity protection for containers and VMs, and has co-authored two books on cloud computing and cloud security.
Raghu Yeluri is an Intel Fellow and Lead Security Architect for Confidential AI and Confidential Computing Services in Intel’s Office of the CTO. He is the chief architect of Intel Trust Authority, Industry's first operator independent multi-cloud attestation service for multi-vendor TEEs and confidential workloads, released in 2023. Over the last decade, he has successfully architected multiple solutions for 'trusted computing' that are broadly deployed in many private and public cloud environments. He is a frequent presenter at technical conferences like Kubecon, OC3, Intel Innovation, IBM Think, VMWorld, etc. on Security. Raghu has 10+ patents in security, attestation, confidentiality/integrity protection for containers and VMs, and has co-authored two books on cloud computing and cloud security.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.