Security Strides Ahead with the 11th Gen Intel vPro mobile platform
Security matters now more than ever. Cyber-attacks are moving down the computing stack. Threats are evolving to evade and obfuscate security software detection methods, and they are using remote worker endpoint PCs as a direct vector into networks, cloud, and SaaS applications. Our latest Intel® Hardware Shield security technologies announced on the new 11th Gen Intel® Core™ vPro® mobile processors aim to stay ahead of bad actors. Security is not a one-time event and must continue to evolve. Today, I am excited to share the story of Intel's unwavering commitment to making exceptional security possible—yesterday, today and tomorrow.
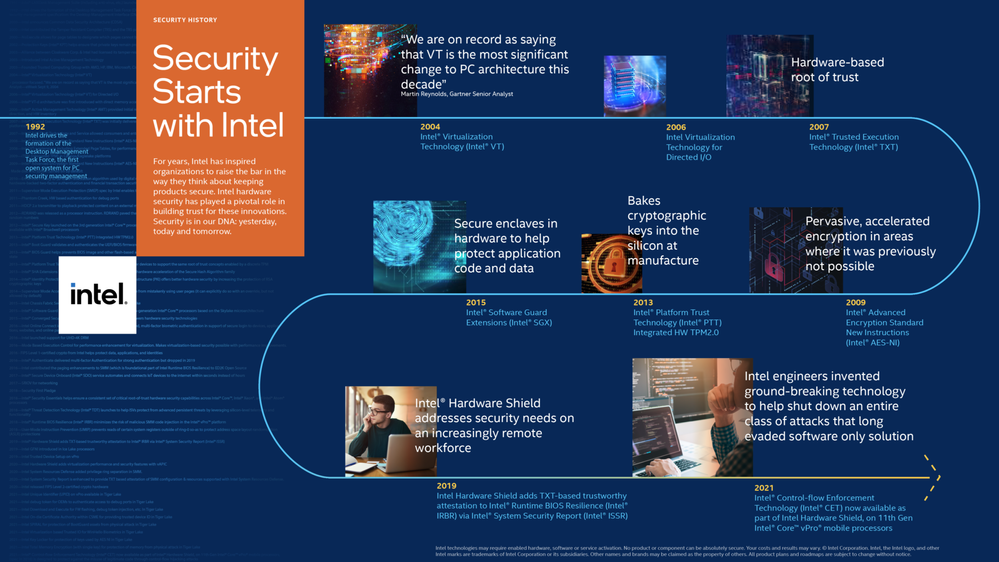
“Security starts with Intel”, as innovative security capabilities have landed first on Intel platforms for decades. We work tirelessly with our partners to stay ahead of tomorrow's cyber-attacks and build security solutions to help solve the toughest security problems.
Our History of Raising the Bar in Security Continues
With the latest Intel vPro mobile platform, Intel Hardware Shield delivers more technology to help ensure defense in depth. Available exclusively on the Intel® Core™ vPro® mobile platform, Intel Hardware Shield provides the world's most comprehensive hardware-based security for business.¹
Now with 11th Gen, our Intel engineers invented ground-breaking technology to help shut down an entire class of attacks that long evaded software only solutions.² Intel also delivers the industry's first silicon-enabled AI threat detection to help stop ransomware and cryptomining attacks.³
Beyond hardware and software technology, Intel has raised the bar on more security assurance—because security is a continuous process, not a one-time event.
Modern Threats Require Defense in Depth
Improved hardware-based security helps to better protect organizations from cyber-threats—software-only solutions no longer suffice. Businesses of all sizes require robust and comprehensive hardware-based security capabilities to help ensure security in-depth—that means protection at each layer: hardware, BIOS/firmware, hypervisor, virtual machines, operating systems, and applications.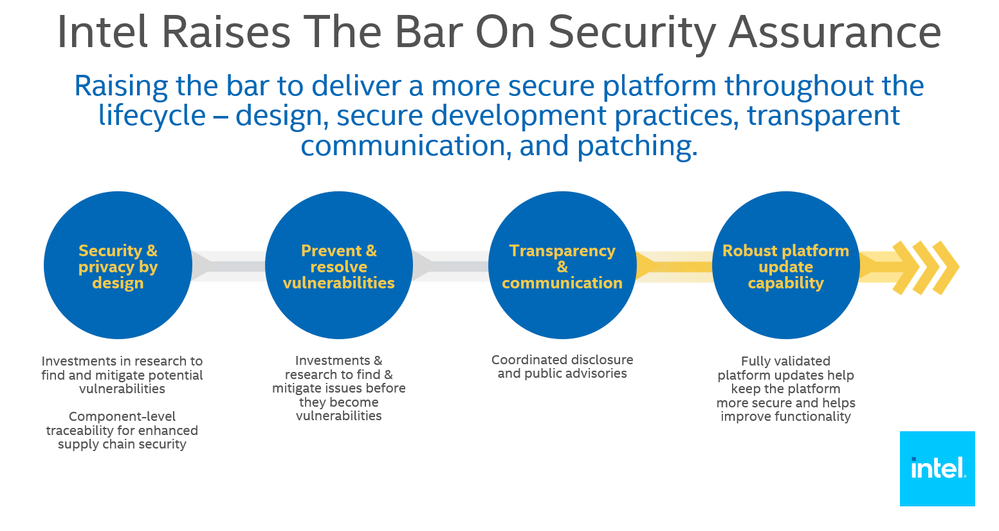
We are proud of our unmatched product security support with industry-leading security processes to help keep your business safe, and we stand behind them relentlessly for our customers. For example, Intel's leading Bug Bounty program invites the security research community to partner, discover, and mitigate issues.⁴ With knowledge gained from that program, as well as extensive research in our labs and with ecosystem partners, Intel builds products with security integrated at every step, backed by dedicated teams evaluating security resilience.⁵ Although no security technologies or practices can provide 100 percent protection, when attacks do happen, Intel has unrivaled product security incident response with coordinated processes to help keep your business safe.⁶
Help Secure your Business with Intel Hardware Shield
Hardware is the bedrock of any security solution, and Intel is uniquely positioned in the industry to create and deliver truly innovative hardware-based security technologies. Intel Hardware Shield innovations built into the Intel vPro platform can help protect PCs from malicious attacks at the foundational level.
Intel Hardware Shield helps ensure that the operating system (OS) runs on legitimate hardware, and it provides hardware-to-software security visibility, empowering the OS to enforce a more complete security policy. In addition, Intel Hardware Shield, in partnership with leading security ISVs, offers application, OS, and data protection, as well as advanced threat detection and protection features that exceed the Microsoft Secure-core PC specification.
Intel Hardware Shield offers a strong feature roadmap that continues to evolve on the 11th Gen Intel Core vPro mobile systems. We think of these features in three categories:
Advanced Threat Detection
Advanced threats elude conventional security solutions using a variety of creative approaches. For example, control-flow hijacking attacks system memory, targeting OSs, browsers, readers and other applications. Attackers use existing code running from executable memory to change program behavior. Intel® Control-flow Enforcement Technology, part of Intel Hardware Shield, helps achieve, hardware-integrated protection with minimal impact on the user experience. Intel worked closely with Microsoft to enable Windows 10 and developer tools, so applications and the industry at large can offer more protection against control-flow hijacking threats.
11th Gen Intel Core vPro processors' telemetry helps security ISVs accelerate AI-based detection of threats like ransomware and cryptomining. According to a June 2020 ZDNet report, "Ransomware is rapidly shaping up to be the defining online security issue of our era." A growing concern is the fact that ransomware has evolved to bypass traditional detection techniques. To address that, Intel® Threat Detection Technology leverages Intel® Iris™ Xe integrated graphics technology, enabling security ISVs to offload advanced memory scanning, AI-based detection, and other performance-intensive security workloads to improve agent-based security processing.
Application and Data Protection
Another set of Intel Hardware Shield features uses hardware-accelerated virtualization and encryption to help eliminate an entire class of attacks that evade current software solutions. Intel® Virtualization Technology is a part of Intel Hardware Shield that accelerates virtualization to help protect applications, data, and OSs without adversely impacting user productivity.
Intel Hardware Shield complements accelerated virtualization with accelerated encryption—protecting data requires hardware-based security capabilities at every layer, including data and system memory encryption. Intel® Advanced Encryption Standard-New Instructions (Intel® AES-NI) improve the performance of the software AES algorithm to accelerate data encryption. Intel AES-NI makes pervasive encryption feasible in areas where previously it was not. And now, Intel® Total Memory Encryption (Intel® TME) encrypts all of the system memory and enables confidentiality of the data in DRAM and on the system memory buses.
Below the OS Security
Hackers have begun targeting firmware, below what the OS or security applications can see and monitor. A compromised PC can offer up access-identity, encryption-keys and passwords, in addition to sensitive data.
Intel Hardware Shield can lock down memory in the UEFI/BIOS against firmware attacks, and it enforces a secure boot at the hardware level. The below-the-OS security features are set-up by the PC manufacturer, so IT departments and users can take advantage of them right out of the box. These below-the-OS technologies include Intel® BIOS Guard, Intel® Boot Guard, Intel Firmware Update/Recovery, Intel® Platform Trust Technology, Intel® Runtime BIOS Resilience, Intel® System Security Report, Intel® System Resources Defense, and Intel® Trusted Execution Technology.
Software Partners
The advanced threat detection features are supported explicitly in Microsoft Windows 10 Enterprise Edition. In addition, the following ISVs use specific Intel TDT capabilities of Intel Hardware Shield as follows:
Microsoft Defender for Endpoint previously announced the enablement of Intel TDT to improve the efficacy of its advanced memory scanning without compromising the user experience.
Blackberry has previously announced the integration of Intel TDT cryptomining detection into BlackBerry® Optics to help users quickly detect cryptojacking at the hardware level.
Cybereason has announced their role as showcase partner that will bring to market Intel TDT enabled ransomware detection solutions. This builds on their long history of first to market innovations on ransomware protection solutions.
SentinelOne previously announced the integration of Intel TDT Accelerated Memory Scanning (AMS) capability to help increase threat detection efficacy without compromising user experience. Intel testing using pre-production SentinelOne Singularity software performing background memory scanning has shown instances where productivity can be improved on an 11th Gen Intel vPro mobile platform—with security offload to Intel Iris Xe Graphics—compared to 10th Gen systems.
Move to Next-Generation Security
Securing your business from cyber-threats requires more than a set of technology features. Intel, with our decades-long commitment to product security throughout the lifecycle, delivers ground-breaking hardware-based capabilities and an unwavering commitment to help eliminate cyber-threats—yesterday, today and tomorrow.
Today, the Intel vPro platform with Intel Hardware Shield breaks new ground in our relentless pursuit of exceptional security for business. To learn more about Intel Hardware Shield, visit https://intel.com/hardwareshield or contact your Intel rep.
Performance varies by use, configuration and other factors. Learn more at www.Intel.com/PerformanceIndex. Performance results are based on testing as of dates shown in configurations and may not reflect all publicly available updates. See backup for configuration details.
No product or component can be absolutely secure.
Your costs and results may vary.
Intel technologies may require enabled hardware, software or service activation.
Intel does not control or audit third-party data. You should consult other sources to evaluate accuracy.
© Intel Corporation. Intel, the Intel logo, and other Intel marks are trademarks of Intel Corporation or its subsidiaries. Other names and brands may be claimed as the property of others.
1 In thin & light Windows-based devices, based on unique features and testing by IOActive (commissioned by Intel; as of December 2020) comparing Intel® Hardware Shield security capabilities with corresponding technologies in an AMD Ryzen Pro 4750U-based system. Visit www.intel.com/11thgenvpro for details. Results may vary.
² Intel Control-flow Enforcement Technology (Intel® CET) is designed to help protect against jump/call-oriented programming (JOP/COP) attack methods and return-oriented programming (ROP) attack methods, malware known as memory safety issues and which comprise over half of ZDI-disclosed vulnerabilities. Visit www.intel.com/11thgenvpro for details. Results may vary.
3 In thin & light Windows-based PCs, based on December 2020 IOActive study (commissioned by Intel) comparing malware detection by Intel 11th Gen Core vPro platform with Intel TDT and AMD Ryzen Pro 4750U-based system. Visit www.intel.com/11thgenvpro for details on Intel's industry-leading CPU behavior monitoring technology. Results may vary.
⁴ Intel is committed to partnering with the security research community to improve product security across the industry. Learn more at www.intel.com/11thgenvpro.
⁵ Intel applies the security development lifecycle from inception to production, with testing from teams of dedicated security experts. Learn more at www.intel.com/11thgenvpro.
⁶ The Intel Platform Update (IPU) process proactively and transparently enables product security updates across the ecosystem, providing vulnerability mitigation for Intel products and customers. Learn more at www.intel.com/11thgenvpro.
 Michael Nordquist is the Vice President Client Computing Group & General Manager, Business Client Product Planning and Architecture. He has overall product planning and architecture responsibility for Intel’s business client platforms, including the Intel® vPro™ brand, across all desktop and mobile platforms. Nordquist has held a variety of sales, marketing, planning, and management roles since joining Intel in 2000. Prior to running product planning for the Business Client Group, he was the director of strategic planning focused on phones, tablets, and our Intel® Atom™ microprocessor. He holds a bachelor’s degree in electrical engineering from the University of Minnesota and an MBA from Babson College.
Michael Nordquist is the Vice President Client Computing Group & General Manager, Business Client Product Planning and Architecture. He has overall product planning and architecture responsibility for Intel’s business client platforms, including the Intel® vPro™ brand, across all desktop and mobile platforms. Nordquist has held a variety of sales, marketing, planning, and management roles since joining Intel in 2000. Prior to running product planning for the Business Client Group, he was the director of strategic planning focused on phones, tablets, and our Intel® Atom™ microprocessor. He holds a bachelor’s degree in electrical engineering from the University of Minnesota and an MBA from Babson College.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.