This is Part 4 of a 5 Part Series
Welcome to the 4th installment of our series. In this post we will cover:
- Building NGINX async mode from source code on Machine-2.
- Testing that the web server responds to http requests on port 80.
- Install SSL certificates on Machine-2.
- Testing that the web server responds to https requests on port 443.
You can get caught up on where we are by reading part 1, part 2 and part 3.
NGINX Installation and Optimization Settings -- Machine-2
In the previous post, the Machine-2 instance got configured with QAT engine for OpenSSL. In this section, we will install NGINX async on the same machine and configure it to be running as a web server which will serve https requests on port 443. Https is a TCP protocol that uses OpenSSL libraries for encrypting and securing web traffic in motion for SSL/TLS.
For this part, we will be building the NGINX binary from the NGINX async source that has been optimized with the QAT engine. Run the steps below.
Build and Configure NGINX Async
Log into the Machine-2 via SSH as "ubuntu" user.
Download NGINX source code
| git clone https://github.com/intel/asynch_mode_nginx.git |
Install dependencies and build and install NGINX
apt-get install build-essential zlib1g zlib1g-dev libssl-dev libpcre3 libpcre3-dev # the build is configured using the configure command. It defines various aspects |
After the configure command finishes successfully, it will show the folder where the various NGINX files will be installed. For the settings we have chosen, the below folders are displayed by the configure command.
| nginx path prefix: "/home/ubuntu/asynch_mode_nginx" nginx binary file: "/usr/bin/nginx" nginx modules path: "/home/ubuntu/asynch_mode_nginx/modules" nginx configuration prefix: "/etc/nginx" nginx configuration file: "/etc/nginx/nginx.conf" nginx pid file: "/var/run/nginx.pid" nginx error log file: "/var/log/nginx/error.log" nginx http access log file: "/var/log/nginx/access.log" nginx http client request body temporary files: "client_body_temp" nginx http proxy temporary files: "proxy_temp" nginx http fastcgi temporary files: "fastcgi_temp" nginx http uwsgi temporary files: "uwsgi_temp" nginx http scgi temporary files: "scgi_temp" |
Build and install from the Makefile
| sudo su make make install |
You can start NGINX by simply typing nginx followed by Enter.
| sudo su nginx |
Verify that nginx is running with ps
| ps aux | grep nginx |
Launch NGINX on Boot
To have NGINX to start at system boot, we can create a service files at /lib/systemd/system/nginx.service with content like this:
| sudo nano /lib/systemd/system/nginx.service |
Paste the following lines of code into the file. Press <CTRL>+X, they type Y and then press Enter. This will save and quit the files you just edited.
| [Unit] Description=The NGINX HTTP and reverse proxy server After=syslog.target network-online.target remote-fs.target nss-lookup.target Wants=network-online.target [Service] Type=forking PIDFile=/var/run/nginx.pid ExecStartPre=/usr/bin/nginx -t ExecStart=/usr/bin/nginx ExecReload=/usr/bin/nginx -s reload ExecStop=/bin/kill -s QUIT $MAINPID PrivateTmp=true [Install] WantedBy=multi-user.target |
Reboot the machine, wait 2 minutes, then log back in via SSH
| sudo reboot |
Enable nginx using systemctl
| sudo systemctl enable nginx |
Test the Web Server
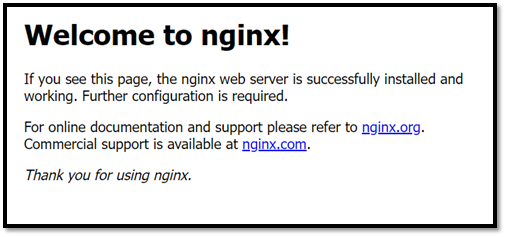
Test that your web server is working. Find the public IP address of Machine-2. Put the IP address on any browser. You should be able to see the default NGINX web server page. It should look like the screenshot below.
Note: In order to be able to hit the NGINX web server from your browser, enable the http (port 80) and https (port 443) on Machine-2's EC2 security group from the source IP, which is the machine on which you will launch the browser.
Install SSL Certificate on NGINX Server -- Machine-2
The NGINX server being set up in the following steps is created on Machine-2. We will install the SSL certificate and the private key in this NGINX server to enable an https connection. To mimic how customers implement web servers in production, this blog uses an SSL certificate and private keys provided by trusted certificate authorities. Self-signed certificates are not being used since that is not how customers implement production web servers. In this example, the certificate is provided by ZeroSSL. You can use other certificate authorities like Digicert or SSL.com.
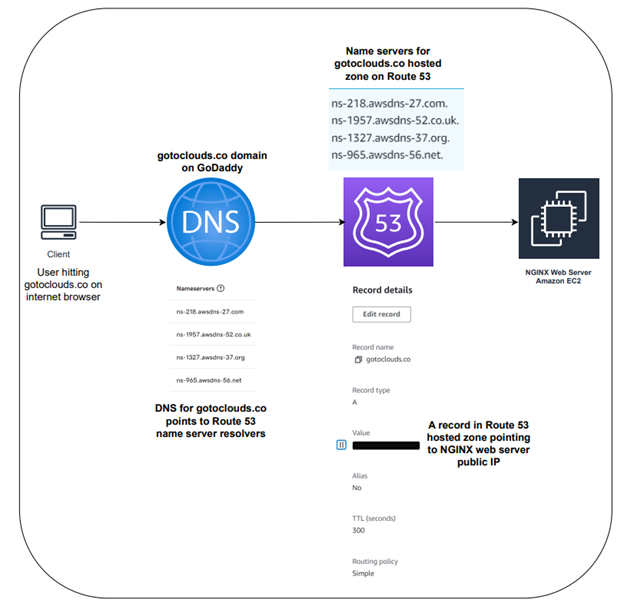
The diagram above shows how the user connects to the NGINX web server and the setup behind it. The user is using the computer called “client” on the left of the diagram. The user enters the domain gotoclouds.co on an internet browser. The request is routed to GoDaddy which is hosting the domain gotoclouds.co. The DNS settings of the domain gotoclouds.co inside GoDaddy is setup with name servers that are pointing to Amazon’s Route 53. The request is routed to Route 53 for DNS resolution. The A record setup inside Route 53 is configured with the public IP address of the NGINX web server. In the diagram, the IP address is blacked out for security reasons. Route 53 routes the request to the NGINX web server that is setup on an EC2 instance within the AWS environment.
Pre-Requisites
To mimic a similar setup, you will need to have these pre-requisites in place. There are reference links below that provide guidance on setting up the pre-requisites.
Pre-requisite Set-up Guidance
- How to set up a domain with a domain registrar, for example, GoDaddy.
- How to create a public hosted zone on Route 53.
- How to create records with Route 53 hosted zone.
- How to manage DNS records in your domain registrar website, for example in GoDaddy.
- How to create SSL certificates from a certificate authority, for example in ZeroSSL.
Set-Up Steps:
- Set up your domain with your domain hosting company of choice.
- Within AWS Route 53 service, set up a hosted zone.
- Add an A record in your hosted zone on Route 53 that will point to the public IP address of your NGINX web server.
- Edit the DNS settings of your domain in the domain hosting company's platform to change the domain name servers to be the name servers from AWS Route 53 hosted zone that your set up in an earlier step.
- Make sure your domain name resolves to the public IP address of the NGINX server.
- From your choice of Certificate Authority, generate a Certificate Signing Request (CSR).
- Once the CSR is approved, generate an SSL certificate.
- Download the private key and certificate files on your local system.
For steps #9 and #10 outlined below, note that if the user is using an SSH client, the user "ubuntu" may not have access to copy files directly into /etc/ssl/private and /etc/ssl/certs folders. In that case, the user can first copy the files into the /home/ubuntu directory. Then SSH into the machine. At that point the "ubuntu" user can assume sudo privilege and copy the files from /home/ubuntu to /etc/ssl/private and /etc/ssl/certs folders. - Copy the private key from your local system to the /ext/ssl/private directory on the NGINX web server you are setting up.
- Copy the certificate files from your local system to the /etc/ssl/certs directory on the NGINX web server you are setting up. In our case, we had a certificate.crt file and a ca-bundle.crt file that was provided from Certificate Authority. We had to concatenate the files together and had to rename the concatenated file as certificate.crt. In the concatenation process, the certificate.crt file went first and the ca_bundle.crt file went after that. We used a command like the one below.
| # Run this command as root cat certificate.crt ca_bundle.crt >> certificate.crt |
Configuration update in NGINX.conf file
Open the nginx.conf file in the editor and paste in the the configurations from this example optimized_nginx.conf. This example configuration has the QAT engine module enabled with the required configuration.
| sudo nano /etc/nginx/nginx.conf |
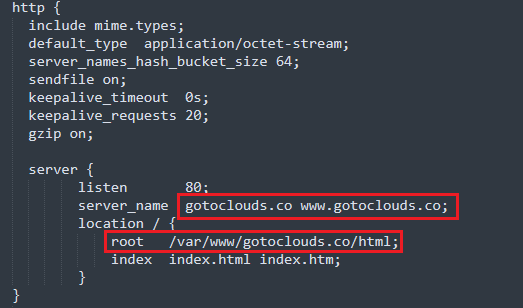
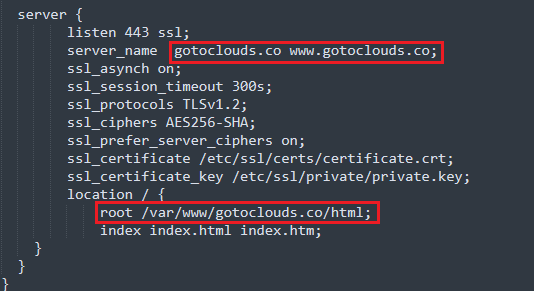
Inside the nginx.conf file, there are a few places where the domain name needs to be updated. In the example nginx.conf file, the domain name is gotoclouds.co. You will need to update the domain names with your domain_name. Below are the places in the nginx.conf file where this needs to be updated.
Image: the places to update in the file are highlighted in red.
Image: the places to update in the file are highlighted in red.
After making the changes, save the file and exit using <CTRL>+X, then Y and then Enter.
Create the following folder structure in your NGINX web server. The domain_name in the path below should be replaced with the name of your own domain.
Note: if any of the directories in the path below do not exist, then those directories also need to be created.
| sudo mkdir /var/www/domain_name/html |
Open an editor to paste the HTML below in to the index.html file. The command to edit the index.html file and the html is provided.
| sudo nano /var/www/domain_name/html/index.html <h1><strong>This is a test page for OPTIMIZED NGINX Web Server. This page is being served securely over HTTPS</strong></h1> <p> </p> <p><em><strong>THANK YOU FOR VISITING !!</strong></em></p> |
Restart NGINX service
| sudo systemctl restart nginx |
Test the Domain Using https://
Test to see if the secured web page is working. Open a browser and put the URL in as https://domain_name. Change the domain name to your domain name. You should be able to see the secured web as below.
Note: In the prior step, you should have already enabled this:
In order to be able to hit the NGINX web server from your browser, you need to enable the http (port 80) and https (port 443) on Machine-2's EC2 security group from the source IP, which is the machine on which you will launch the browser.
Now that we have built the NGINX async mode from source code and optimized settings on Machine-2, we are ready to move onto Part 5: Installing non-optimized NIGINX on Machine-1, run benchmark tests on both machines and compare the results to see the performance improvement coming from Intel's Crypto NI instructions.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.