- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
my device:
intel a750 gpu card
i5-13600KF
msi m760 ddr4 16g x4
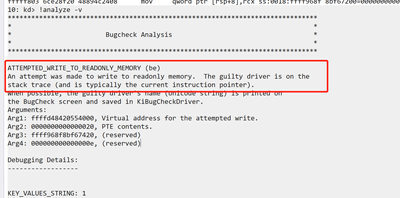
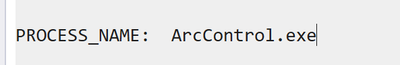
Microsoft (R) Windows Debugger Version 10.0.25200.1003 AMD64 Copyright (c) Microsoft Corporation. All rights reserved. Loading Dump File [C:\Windows\Minidump\011623-6234-01.dmp] Mini Kernel Dump File: Only registers and stack trace are available ************* Path validation summary ************** Response Time (ms) Location Deferred srv* Symbol search path is: srv* Executable search path is: Windows 10 Kernel Version 22621 MP (20 procs) Free x64 Product: WinNt, suite: TerminalServer SingleUserTS Machine Name: Kernel base = 0xfffff803`6ca00000 PsLoadedModuleList = 0xfffff803`6d613010 Debug session time: Mon Jan 16 22:48:11.193 2023 (UTC + 8:00) System Uptime: 0 days 12:26:31.873 Loading Kernel Symbols .. Press ctrl-c (cdb, kd, ntsd) or ctrl-break (windbg) to abort symbol loads that take too long. Run !sym noisy before .reload to track down problems loading symbols. ............................................................. ................................................................ ................................................................ ....................... Loading User Symbols Loading unloaded module list ......... For analysis of this file, run !analyze -v nt!KeBugCheckEx: fffff803`6ce28f20 48894c2408 mov qword ptr [rsp+8],rcx ss:0018:ffff968f`8bf67200=00000000000000be 10: kd> !analyze -v ******************************************************************************* * * * Bugcheck Analysis * * * ******************************************************************************* ATTEMPTED_WRITE_TO_READONLY_MEMORY (be) An attempt was made to write to readonly memory. The guilty driver is on the stack trace (and is typically the current instruction pointer). When possible, the guilty driver's name (Unicode string) is printed on the BugCheck screen and saved in KiBugCheckDriver. Arguments: Arg1: ffffd48420554000, Virtual address for the attempted write. Arg2: 0000000000000020, PTE contents. Arg3: ffff968f8bf67420, (reserved) Arg4: 000000000000000e, (reserved) Debugging Details: ------------------ KEY_VALUES_STRING: 1 Key : Analysis.CPU.mSec Value: 828 Key : Analysis.DebugAnalysisManager Value: Create Key : Analysis.Elapsed.mSec Value: 1108 Key : Analysis.IO.Other.Mb Value: 0 Key : Analysis.IO.Read.Mb Value: 0 Key : Analysis.IO.Write.Mb Value: 0 Key : Analysis.Init.CPU.mSec Value: 218 Key : Analysis.Init.Elapsed.mSec Value: 23174 Key : Analysis.Memory.CommitPeak.Mb Value: 107 Key : Bugcheck.Code.DumpHeader Value: 0xbe Key : Bugcheck.Code.Register Value: 0xbe Key : Dump.Attributes.AsUlong Value: 1008 Key : Dump.Attributes.DiagDataWrittenToHeader Value: 1 Key : Dump.Attributes.ErrorCode Value: 0 Key : Dump.Attributes.KernelGeneratedTriageDump Value: 1 Key : Dump.Attributes.LastLine Value: Dump completed successfully. Key : Dump.Attributes.ProgressPercentage Value: 0 FILE_IN_CAB: 011623-6234-01.dmp DUMP_FILE_ATTRIBUTES: 0x1008 Kernel Generated Triage Dump BUGCHECK_CODE: be BUGCHECK_P1: ffffd48420554000 BUGCHECK_P2: 20 BUGCHECK_P3: ffff968f8bf67420 BUGCHECK_P4: e BLACKBOXBSD: 1 (!blackboxbsd) BLACKBOXNTFS: 1 (!blackboxntfs) BLACKBOXPNP: 1 (!blackboxpnp) BLACKBOXWINLOGON: 1 CUSTOMER_CRASH_COUNT: 1 PROCESS_NAME: ArcControl.exe TRAP_FRAME: ffff968f8bf67420 -- (.trap 0xffff968f8bf67420) NOTE: The trap frame does not contain all registers. Some register values may be zeroed or incorrect. rax=ffffd48420552800 rbx=0000000000000000 rcx=ffffd48420554010 rdx=00002d8d7779a040 rsi=0000000000000000 rdi=0000000000000000 rip=ffffff26d02f2d53 rsp=ffff968f8bf675b8 rbp=ffff968f8bf67750 r8=0000000000000030 r9=000000000000008f r10=fffff8041e9e76d8 r11=0000021197cf0440 r12=0000000000000000 r13=0000000000000000 r14=0000000000000000 r15=0000000000000000 iopl=0 nv up ei pl nz ac pe nc win32kfull!memcpy+0x113: ffffff26`d02f2d53 0f2941f0 movaps xmmword ptr [rcx-10h],xmm0 ds:ffffd484`20554000=???????????????????????????????? Resetting default scope STACK_TEXT: ffff968f`8bf671f8 fffff803`6ce81e71 : 00000000`000000be ffffd484`20554000 00000000`00000020 ffff968f`8bf67420 : nt!KeBugCheckEx ffff968f`8bf67200 fffff803`6cc575cc : fffff803`6d6695c0 00000000`00000002 ffff968f`8bf673b9 00000000`00000000 : nt!MiSystemFault+0x22d7c1 ffff968f`8bf67300 fffff803`6ce39b29 : ffffd483`fbc6f470 ffffff26`cf0853b7 fffff804`1e9e76d8 00000000`00001001 : nt!MmAccessFault+0x29c ffff968f`8bf67420 ffffff26`d02f2d53 : ffffff26`d026b46a ffff968f`8bf677f0 00000000`00000000 fffff803`ce80aab8 : nt!KiPageFault+0x369 ffff968f`8bf675b8 ffffff26`d026b46a : ffff968f`8bf677f0 00000000`00000000 fffff803`ce80aab8 ffffff26`cf050646 : win32kfull!memcpy+0x113 ffff968f`8bf675c0 ffffff26`d026b22a : fffff804`1e9e76c0 00000000`00000000 00000000`00003c00 fffff803`00003c00 : win32kfull!bDoGetSetBitmapBits+0x132 ffff968f`8bf67650 ffffff26`d026b0ab : 00000000`00000000 00000000`00000870 00000000`00000f00 00000000`00000006 : win32kfull!GreSetBitmapBitsInternal+0x172 ffff968f`8bf677d0 ffffff26`cf015d74 : ffff968f`8bf67a01 ffffff26`00000000 00000000`00000000 00000000`00000000 : win32kfull!GreSetBitmapBits+0x2b ffff968f`8bf67820 ffffff26`d0270fe1 : ffff968f`00000000 00000000`00000000 00000000`00000020 00000000`00000870 : win32kbase!GreCreateBitmapInternal+0x374 ffff968f`8bf678f0 ffffff26`cf54adec : ffffc18f`78a96080 ffff968f`8bf67aa0 00000040`498fde88 ffff968f`8bf679c8 : win32kfull!NtGdiCreateBitmap+0x61 ffff968f`8bf67970 fffff803`6ce3dce5 : 00000000`00000000 ffffff26`d02ade44 00000000`00000040 aaaaaaaa`aaaaaaaa : win32k!NtGdiCreateBitmap+0x20 ffff968f`8bf679b0 00007fff`802a2174 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x25 00000040`498fde68 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x00007fff`802a2174 SYMBOL_NAME: win32kfull!memcpy+113 MODULE_NAME: win32kfull IMAGE_NAME: win32kfull.sys IMAGE_VERSION: 10.0.22621.1105 STACK_COMMAND: .cxr; .ecxr ; kb BUCKET_ID_FUNC_OFFSET: 113 FAILURE_BUCKET_ID: AV_win32kfull!memcpy OSPLATFORM_TYPE: x64 OSNAME: Windows 10 FAILURE_ID_HASH: {23cab79c-0979-b42a-ec0e-d7a3379768ec} Followup: MachineOwner ---------
outpu
Link Copied
0 Replies
Reply
Topic Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page