- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Intel SGX provides a remote attestation, which means that the client can trust the program running in the Enclave of the SGX application running on the server. However, since the communication between the client and server runs in the untrusted area, I believe that the client cannot guarantee that the data sent by the client will be processed correctly (e.g., a process in the untrusted area is tampered with and does not transition into the Enclave). Is this correct?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
In order for Remote Attestation to work, the client's enclave must proves the following:
- The identity
- That it has not been tampered with
- That it is running on a genuine platform with Intel SGX enabled
- That it is running at the latest security level, also referred to as the Trusted Computing Base (TCB) level
After all these conditions are met, only then is a connection between client and server established and the remote server can safely provision secrets to the enclave.
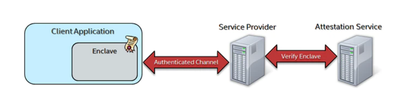
The Remote Attestation utilizes a modified Sigma protocol to facilitate a Diffie-Hellman Key Exchange (DHKE) between the client and server. The shared key obtained from this exchange can be used by the service provider to encrypt secrets to be provisioned to the client. The client enclave is able to derive the same key and use it to decrypt the secret.
Here is the complete attestation flow figure for your reference.
Refer this Article (Provisioning Secrets with Remote Attestation) for more information. Hope this is helpful.
Regards,
Ken
Link Copied
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
In order for Remote Attestation to work, the client's enclave must proves the following:
- The identity
- That it has not been tampered with
- That it is running on a genuine platform with Intel SGX enabled
- That it is running at the latest security level, also referred to as the Trusted Computing Base (TCB) level
After all these conditions are met, only then is a connection between client and server established and the remote server can safely provision secrets to the enclave.
The Remote Attestation utilizes a modified Sigma protocol to facilitate a Diffie-Hellman Key Exchange (DHKE) between the client and server. The shared key obtained from this exchange can be used by the service provider to encrypt secrets to be provisioned to the client. The client enclave is able to derive the same key and use it to decrypt the secret.
Here is the complete attestation flow figure for your reference.
Refer this Article (Provisioning Secrets with Remote Attestation) for more information. Hope this is helpful.
Regards,
Ken
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Thank you for your question and the accepted solution. Hope the information provided is helpful. If you need any additional information from Intel, please submit a new question as this thread is no longer being monitored.
Regards,
Ken
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page