- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Problems:
- can not get platform manifest
- cannot generate quote in remote-attestation
The problems I encountered are very similar to this article: https://community.intel.com/t5/Intel-Software-Guard-Extensions/Remote-attestation-not-possible-request-guidance/td-p/1380901
but there are some differences:
- My machine has multi-package CPU
- there is no `PCK selection library returned 12` in my PCCS log
My Environment:
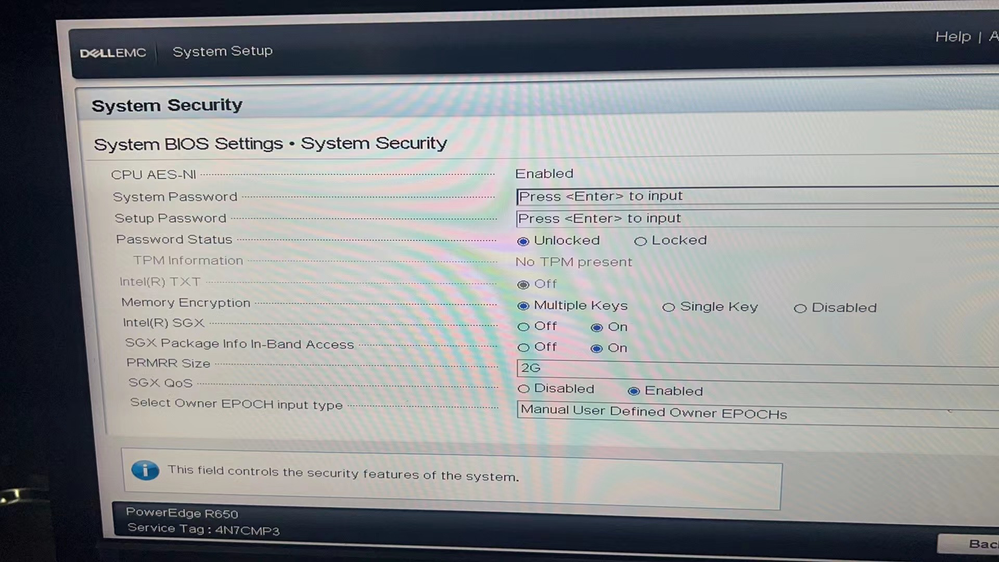
BIOS:
uname -r
5.13.4
lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 20.04.4 LTS
Release: 20.04
Codename: focal
apt list --installed | grep -i sgx
WARNING: apt does not have a stable CLI interface. Use with caution in scripts.
libsgx-ae-epid/unknown,now 2.17.100.3-focal1 amd64 [installed,automatic]
libsgx-ae-id-enclave/unknown,now 1.14.100.3-focal1 amd64 [installed,automatic]
libsgx-ae-le/unknown,now 2.17.100.3-focal1 amd64 [installed,automatic]
libsgx-ae-pce/unknown,now 2.17.100.3-focal1 amd64 [installed,automatic]
libsgx-ae-qe3/unknown,now 1.14.100.3-focal1 amd64 [installed,automatic]
libsgx-aesm-ecdsa-plugin/unknown,now 2.17.100.3-focal1 amd64 [installed,automatic]
libsgx-aesm-epid-plugin/unknown,now 2.17.100.3-focal1 amd64 [installed,automatic]
libsgx-aesm-launch-plugin/unknown,now 2.17.100.3-focal1 amd64 [installed,automatic]
libsgx-aesm-pce-plugin/unknown,now 2.17.100.3-focal1 amd64 [installed,automatic]
libsgx-aesm-quote-ex-plugin/unknown,now 2.17.100.3-focal1 amd64 [installed,automatic]
libsgx-dcap-default-qpl/unknown,now 1.14.100.3-focal1 amd64 [installed]
libsgx-enclave-common/unknown,now 2.17.100.3-focal1 amd64 [installed,automatic]
libsgx-epid/unknown,now 2.17.100.3-focal1 amd64 [installed]
libsgx-launch/unknown,now 2.17.100.3-focal1 amd64 [installed]
libsgx-pce-logic/unknown,now 1.14.100.3-focal1 amd64 [installed,automatic]
libsgx-qe3-logic/unknown,now 1.14.100.3-focal1 amd64 [installed,automatic]
libsgx-quote-ex/unknown,now 2.17.100.3-focal1 amd64 [installed]
libsgx-ra-network-dbgsym/now 1.14.100.3-focal1 amd64 [installed,upgradable to: 1.14.100.3-focal1]
libsgx-ra-network-dev/unknown,now 1.14.100.3-focal1 amd64 [installed]
libsgx-ra-network/unknown,now 1.14.100.3-focal1 amd64 [installed]
libsgx-ra-uefi-dbgsym/unknown,now 1.14.100.3-focal1 amd64 [installed]
libsgx-ra-uefi-dev/unknown,now 1.14.100.3-focal1 amd64 [installed]
libsgx-ra-uefi/unknown,now 1.14.100.3-focal1 amd64 [installed]
libsgx-urts/unknown,now 2.17.100.3-focal1 amd64 [installed]
sgx-aesm-service/unknown,now 2.17.100.3-focal1 amd64 [installed,automatic]
sgx-dcap-pccs/unknown,now 1.13.100.4-focal1 amd64 [installed,upgradable to: 1.14.100.3-focal1]
sgx-pck-id-retrieval-tool/unknown,now 1.14.100.3-focal1 amd64 [installed]
sgx-ra-service-dbgsym/now 1.14.100.3-focal1 amd64 [installed,upgradable to: 1.14.100.3-focal1]
sgx-ra-service/unknown,now 1.14.100.3-focal1 amd64 [installed]apt list --installed | grep -i dcap
WARNING: apt does not have a stable CLI interface. Use with caution in scripts.
libsgx-dcap-default-qpl/unknown,now 1.14.100.3-focal1 amd64 [installed]
sgx-dcap-pccs/unknown,now 1.13.100.4-focal1 amd64 [installed,upgradable to: 1.14.100.3-focal1]PCCS log:
Jun 24 08:34:21 ubuntu node[43363]: 2022-06-24 08:34:21.870 [info]: 127.0.0.1 - - [24/Jun/2022:08:34:21 +0000] "POST /sgx/certification/v3/platforms HTTP/1.1" 404 32 "-" "-"Jun 24 08:34:46 ubuntu node[43363]: 2022-06-24 08:34:46.284 [info]: Client Request-ID : e95c26e58f0945d4a741d6c0d34adbdb
Jun 24 08:34:47 ubuntu node[43363]: 2022-06-24 08:34:47.547 [info]: Request-ID is : 8b85ef938d17466e906e1bdff584a492Jun 24 08:34:47 ubuntu node[43363]: 2022-06-24 08:34:47.548 [error]: Intel PCS server returns error.
Jun 24 08:34:47 ubuntu node[43363]: 2022-06-24 08:34:47.548 [error]: Error: No cache data for this platform.Jun 24 08:34:47 ubuntu node[43363]: at Proxy.getPckCertFromPCS (/opt/intel/sgx-dcap-pccs/services/logic/commonCacheLogic.js:87:11)
Jun 24 08:34:47 ubuntu node[43363]: at processTicksAndRejections (internal/process/task_queues.js:95:5)Jun 24 08:34:47 ubuntu node[43363]: at async LazyCachingMode.registerPlatforms (/opt/intel/sgx-dcap-pccs/services/caching_modes/cachingMode.js:163:7)
Jun 24 08:34:47 ubuntu node[43363]: at async Proxy.registerPlatforms (/opt/intel/sgx-dcap-pccs/services/platformsRegService.js:107:3)
Jun 24 08:34:47 ubuntu node[43363]: at async postPlatforms (/opt/intel/sgx-dcap-pccs/controllers/platformsController.js:40:5)Run PCK Provisioning tool
PCKIDRetrievalTool
Intel(R) Software Guard Extensions PCK Cert ID Retrieval Tool Version 1.14.100.3
Warning: platform manifest is not available or current platform is not multi-package platform.
Error: unexpected error happend during sending data to cache server.
pckid_retrieval.csv has been generated successfully, however the data couldn't be sent to cache server!cpuid | grep -i sgx
SGX: Software Guard Extensions supported = true
SGX_LC: SGX launch config supported = true
Software Guard Extensions (SGX) capability (0x12/0):
SGX1 supported = true
SGX2 supported = true
SGX ENCLV E*VIRTCHILD, ESETCONTEXT = false
SGX ENCLS ETRACKC, ERDINFO, ELDBC, ELDUC = false
SGX attributes (0x12/1):
SGX EPC enumeration (0x12/n):
SGX: Software Guard Extensions supported = true
SGX_LC: SGX launch config supported = true
Software Guard Extensions (SGX) capability (0x12/0):
SGX1 supported = true
SGX2 supported = true
SGX ENCLV E*VIRTCHILD, ESETCONTEXT = false
SGX ENCLS ETRACKC, ERDINFO, ELDBC, ELDUC = false
SGX attributes (0x12/1):
SGX EPC enumeration (0x12/n):
SGX: Software Guard Extensions supported = true
SGX_LC: SGX launch config supported = true
Software Guard Extensions (SGX) capability (0x12/0):
SGX1 supported = true
SGX2 supported = true
SGX ENCLV E*VIRTCHILD, ESETCONTEXT = false
SGX ENCLS ETRACKC, ERDINFO, ELDBC, ELDUC = false
SGX attributes (0x12/1):
SGX EPC enumeration (0x12/n):
SGX: Software Guard Extensions supported = true
SGX_LC: SGX launch config supported = true
Software Guard Extensions (SGX) capability (0x12/0):
SGX1 supported = true
SGX2 supported = true
SGX ENCLV E*VIRTCHILD, ESETCONTEXT = false
SGX ENCLS ETRACKC, ERDINFO, ELDBC, ELDUC = false
SGX attributes (0x12/1):
SGX EPC enumeration (0x12/n):
SGX: Software Guard Extensions supported = true
SGX_LC: SGX launch config supported = true
Software Guard Extensions (SGX) capability (0x12/0):
SGX1 supported = true
SGX2 supported = true
SGX ENCLV E*VIRTCHILD, ESETCONTEXT = false
SGX ENCLS ETRACKC, ERDINFO, ELDBC, ELDUC = false
SGX attributes (0x12/1):
SGX EPC enumeration (0x12/n):
SGX: Software Guard Extensions supported = true
SGX_LC: SGX launch config supported = true
Software Guard Extensions (SGX) capability (0x12/0):
SGX1 supported = true
SGX2 supported = true
SGX ENCLV E*VIRTCHILD, ESETCONTEXT = false
SGX ENCLS ETRACKC, ERDINFO, ELDBC, ELDUC = false
SGX attributes (0x12/1):
SGX EPC enumeration (0x12/n):
SGX: Software Guard Extensions supported = true
SGX_LC: SGX launch config supported = true
Software Guard Extensions (SGX) capability (0x12/0):
SGX1 supported = true
SGX2 supported = true
SGX ENCLV E*VIRTCHILD, ESETCONTEXT = false
SGX ENCLS ETRACKC, ERDINFO, ELDBC, ELDUC = false
SGX attributes (0x12/1):
SGX EPC enumeration (0x12/n):
SGX: Software Guard Extensions supported = true
SGX_LC: SGX launch config supported = true
Software Guard Extensions (SGX) capability (0x12/0):
SGX1 supported = true
SGX2 supported = true
SGX ENCLV E*VIRTCHILD, ESETCONTEXT = false
SGX ENCLS ETRACKC, ERDINFO, ELDBC, ELDUC = false
SGX attributes (0x12/1):
SGX EPC enumeration (0x12/n):
SGX: Software Guard Extensions supported = true
...run sample:
/opt/intel/sgxsdk/SampleCode/RemoteAttestation# LD_LIBRARY_PATH=$LD_LIBRARY_PATH:$PWD/sample_libcrypto ./app
First round, we will try ECDSA algorithm.
Call sgx_get_extended_epid_group_id success.
MSG0 body generated -
4 bytes:
{
0x0, 0x0, 0x0, 0x0
}
Sending msg0 to remote attestation service provider.
Sent MSG0 to remote attestation service.
Call sgx_select_att_key_id success.
Call sgx_create_enclave success.
Call enclave_init_ra success.
Error, call sgx_ra_get_msg1_ex fail [main].
Call enclave_ra_close success.
Second round, we will try EPID algorithm.
Call sgx_get_extended_epid_group_id success.
MSG0 body generated -
4 bytes:
{
0x0, 0x0, 0x0, 0x0
}
Sending msg0 to remote attestation service provider.
Sent MSG0 to remote attestation service.
Call sgx_select_att_key_id success.
Call sgx_create_enclave success.
Call enclave_init_ra success.
Error, call sgx_ra_get_msg1_ex fail [main].
Call enclave_ra_close success.
Enter a character before exit ../opt/intel/sgx-pck-id-retrieval-tool/network_setting.conf
PCCS_URL=https://localhost:8081/sgx/certification/v3/platforms
USE_SECURE_CERT=FALSE
user_token = <my_plaintext_password>/etc/sgx_default_qcnl.conf
//PCCS server address
"pccs_url": "https://localhost:8081/sgx/certification/v3/",
// To accept insecure HTTPS certificate, set this option to false
"use_secure_cert": false,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Laisky,
This is actually by design, if the platform manifest has been read once byour tools (Multipackage Registration Agent (MPA) or PCK Cert ID Retrieval Tool). Those tools set the SgxRegistrationStatus.Status bit = 1, which instructs the BIOsS to not present the platform manifest in subsequent reboots. You will need to do an SGX Factory Reset in the BIOS, as mentioned here in the Dell R650 BIOS docs.
This will regenerate a new platform keys and re create the platform manifest which can then be used to register the platform. But be aware since this does create new platform keys, any data sealed with the previous platform keys will no longer be accessible/unsealable. You can find more info in our SGX MP SW Doc.
Of course, non of the tools will work if this is not a UEFI install (a legacy BIOS install) as the UEFI variables wouldn't be available which is where the platform manifest is presented to SW.
I hope this is helpful.
Sincerely,
Sahira
Link Copied
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Laisky,
I'm looking into this issue right now. It seems this is a recurring issue for many. I'll let you know what I find.
Sincerely,
Sahira
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I also did some research and someone said that the MPA should output a log of attempts to register after booting the machine, but there is nothing in my MPA.
journalctl -u mpa_registration_tool.service
-- Logs begin at Tue 2022-06-14 01:27:03 UTC, end at Thu 2022-07-07 02:46:30 UTC. --
Jun 24 02:39:43 ubuntu systemd[1]: Started Intel MPA Registration.
Jun 24 02:39:43 ubuntu systemd[1]: mpa_registration_tool.service: Succeeded.
Jun 24 02:40:35 ubuntu systemd[1]: Started Intel MPA Registration.
Jun 24 02:40:35 ubuntu systemd[1]: mpa_registration_tool.service: Succeeded.
-- Reboot --
Jun 24 05:41:41 ubuntu systemd[1]: Started Intel MPA Registration.
Jun 24 05:41:43 ubuntu systemd[1]: mpa_registration_tool.service: Succeeded.
Jun 24 07:35:39 ubuntu systemd[1]: Started Intel MPA Registration.
Jun 24 07:35:39 ubuntu systemd[1]: mpa_registration_tool.service: Succeeded.
Jun 24 08:14:18 ubuntu systemd[1]: Started Intel MPA Registration.
Jun 24 08:14:18 ubuntu systemd[1]: mpa_registration_tool.service: Succeeded.
Jun 30 02:01:22 ubuntu systemd[1]: Started Intel MPA Registration.
Jun 30 02:01:22 ubuntu systemd[1]: mpa_registration_tool.service: Succeeded.
-- Reboot --
Jul 06 01:59:42 ubuntu systemd[1]: Started Intel MPA Registration.
Jul 06 01:59:44 ubuntu systemd[1]: mpa_registration_tool.service: Succeeded.- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Laisky,
This is actually by design, if the platform manifest has been read once byour tools (Multipackage Registration Agent (MPA) or PCK Cert ID Retrieval Tool). Those tools set the SgxRegistrationStatus.Status bit = 1, which instructs the BIOsS to not present the platform manifest in subsequent reboots. You will need to do an SGX Factory Reset in the BIOS, as mentioned here in the Dell R650 BIOS docs.
This will regenerate a new platform keys and re create the platform manifest which can then be used to register the platform. But be aware since this does create new platform keys, any data sealed with the previous platform keys will no longer be accessible/unsealable. You can find more info in our SGX MP SW Doc.
Of course, non of the tools will work if this is not a UEFI install (a legacy BIOS install) as the UEFI variables wouldn't be available which is where the platform manifest is presented to SW.
I hope this is helpful.
Sincerely,
Sahira
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you very much for your kind help.
The problem is due to not setting the BIOS correctly.
I was unable to locate the problem because I didn't have access to the physical machine, but I contacted OPS later to resolve the issue.
Steps:
- reset SGX Factory Reset
- reboot
- Enable SGX Auto MP Registration Agent
- reboot

Another problem I found is that my OS is not booted with UEFI. `/sys/firmware/efi` This path should be present.
After reinstalling the OS with UEFI, everything works fine.
The problem can be located through the logging file: /var/log/mpa_registration.log
Thanks
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page