- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
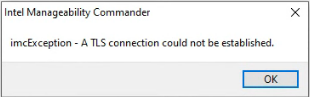
I have a Dell Precision 3460 with AMT 16.1. This version now requires the use of TLS. When I attempt to connect to this device using Intel Manageability Commander, an error message is displayed stating "imcException - A TLS connection could not be established".
MeshCommander however connects with no problem. Likewise, I can connect via web browser via HTTPS on port 16993.
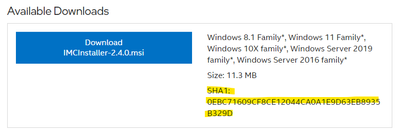
Manageability Commander is the latest version (2.4) installed using the IMCInstaller-2.4.0.msi, although the interface reports that it's 2.3. I suspect this is just a developer oversight.
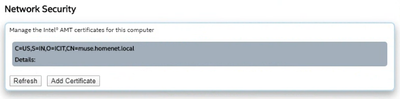
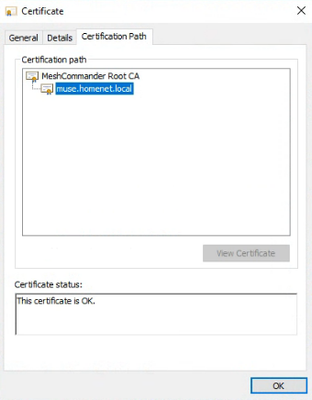
See attached screenshot of AMT embedded certificate as reported by MeshCommander. No obvious issues there.
Any ideas why IMC won't connect?
Link Copied
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, ICIT,
I hope this email finds you well.
The certificate issue experienced is expected on endpoints with AMT version 16.X. Self-Certificates are not supported anymore. There is a note at the button of the Intel® Manageability Commander (IMC) download website and in the release note PDF.
Note: Trying to connect to a target system that uses self-signed TLS certificates will result in an error. This is an expected behavior.
Intel® Manageability Commander download page
https://www.intel.com/content/www/us/en/download/18796/intel-manageability-commander.html
The troubleshooting is acquiring a third-party Intel® AMT Certificate from authorized Intel Certificate vendors.
Vendor Certificates to Support Intel® AMT
MeshCommander supports self-Certificates.
I was able to install the latest version of IMC version 2.4, no issues were experienced, my PC is running Wind 10. Please retry using the instructions in section 2 - Installing and Uninstalling, of the user guide.
https://downloadmirror.intel.com/27807/Intel%20Manageability%20Commander%20User%20Guide.pdf#page=5
I will gladly provide further assistance if necessary.
Regards,
Miguel C.
Intel Customer Support Technician
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Got it, thanks. I overlooked the note about connection errors with self-signed TLS certificates.
For your installation of IMC v2.4, when you go to Help > About, what version number is reported?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, ICIT,
My IMC says 2.4 in the help section. Did you have the previous version 2.3 on your server?
The latest version of the electron is v25.3.0
https://github.com/electron/electron/releases/tag/v25.3.0
I look forward to hearing from you.
Regards,
Miguel C.
Intel Customer Support Technician
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
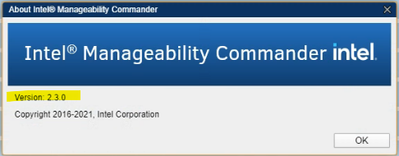
Hmmm. I uninstalled per the IMC user guide, which is basically just using the Control Panel > Programs > Uninstall a Program function in Windows. I then deleted the C:\Program Files (x86)\Intel\Intel Manageability Commander directory and re-ran the IMCInstaller-2.4.0.msi installer. Note that I checked the SHA1 hash to confirm that my installer wasn't modified/corrupted. Before doing the post-install action of copying Electron to the IMC directory, I looked a few files in there. Here are the first few lines of C:\Program Files (x86)\Intel\Intel Manageability Commander\resources\app\package.json
"name": "imc",
"version": "2.3.0",
"description": "Intel(R) Active Management Technology console tool",
"main": "main-electron.js",
"author": "Intel Corporation",
"copyright": "Copyright 2016-2021, Intel Corporation",
Not sure if that's supposed to be 2.3.0 or 2.4.0, I would assume the latter. I then copied Electron to the IMC directory per the instructions in the ReadMe-PostInstall.txt file, which references electron-v8.5.5-win32-ia32.zip. Note that the v2.4 IMC user guide states...
Note: Intel MC is tested and verified only with version 8.5.5 of electron (for Win32 and IA32). Use this ver-sion for both 32 bit and 64 bit platforms. Other versions of electron are not tested or supported.
1. In a web browser, go to https://github.com/electron/electron/releases/tag/v8.5.5.
2. Scroll down and select electron-v8.5.5-win32-ia32.zip (see note above). The file is downloaded to your system.
Are you running it with v25.3.0?
In any event, when I launch and go to Help > About it still reports v2.3. I did have a previous version installed before all of this although I don't recall which specific version.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, ICIT,
I hope all is well.
The tests were performed with both electron versions. The only difference is with the option SHA1. Intel has improved the security with the latest version, only TLS connections are supported, and SHA256 is a requirement. Please try with the option unchecked.
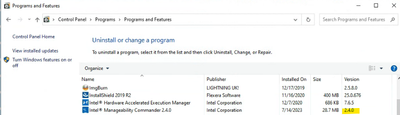
I am pasting a picture of what I have from add or remove a program.
Regards,
Miguel C.
Intel Customer Support Technician
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In Add and Remove Programs on my computer it also shows as v2.4. It's the application GUI where it reports as v2.3. If you go to IMC and select Help > About does is show 2.3 or 2.4?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
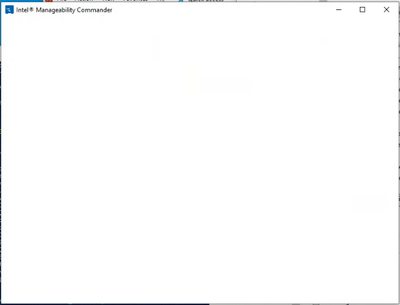
BTW, I uninstalled IMC again and reinstalled using Electron v25.3.0. When I launch IMC it just shows a blank window.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
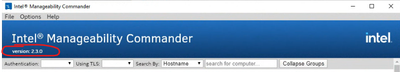
After another uninstall and reinstall using Electron 8.5.5, I'm back where I started. IMC is running but still reports v2.3.0 in the UI.
And under Help > About
In Windows Control Panel > Programs and Features it does report as v2.4
So I'm working under the assumption that this is just a UI issue where a version number was not updated in a source file somewhere and likely not a concern regarding functionality.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
*Duplicate*
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Getting back to the original issue of IMC displaying an error when connecting using TLS...
Initially was attempting to connect with AMT configured using the embedded self-signed TLS certificate, which, as noted above, is not supported by IMC.
To use TLS to connect to an AMT client using IMC, the following must be in place...
- The hostname must be set to a FQDN, IP address cannot be used
- Use TLS enabled
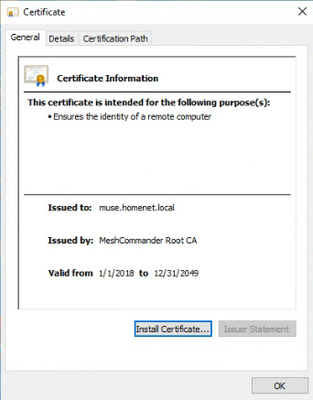
- A certificate must be installed on the AMT device with the Subject CN set to match the FQDN of the device
* Screenshot of certificate in Windows
* Screenshot showing above certificate installed an AMT device
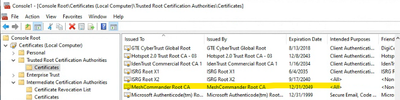
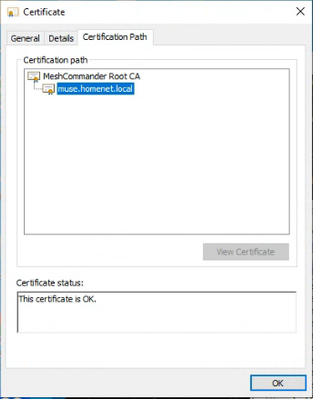
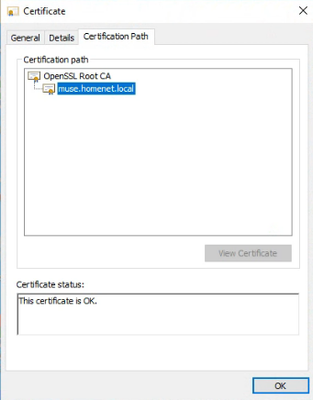
- The root CA certificate (issuer certificate) must be installed in the Trusted Root Certificate store on the Windows computer where IMC is running. This enables IMC to trust the certificate installed on the AMT device
* Screenshot showing the certificate is indeed trusted on the Windows computer where IMC is running
- IMC v2.4 supports TLS 1.1 and newer, it does not support TLS 1.0. TLS 1.1 was implemented in AMT 11.6 so the connection must be to a computer running this version of AMT firmware or newer.
All of the above is in place however I still receive the same connection error.
To troubleshoot further I launched IMC in debug mode from the command line
C:\Program Files (x86)\Intel\Intel Manageability Commander\electron.exe --loglevel=debug
This generates debug level messages in the log file located here
C:\Users\Username\AppData\Roaming\Intel\Intel Manageability Commander\application.log
From these messages I gather that IMC receives the certificate from the AMT device and saves it as tempCert.cer. It then runs
certutil -verify
to get details and checks the hostname against the Subject CN
{"level":"debug","message":"Setting up connection: host=muse.homenet.local; port=16993; authMode=0; username=admin; password=mypassword; useKerberos=false; tls=true"}
{"level":"verbose","message":"Getting AMT class CIM_SoftwareIdentity"}
{"level":"debug","message":"Writing TLS cert temp file: C:\\Users\\USER~1\\AppData\\Local\\Temp\\tempCert.cer"}
{"level":"verbose","message":"CertUtil output: \r\nIssuer:\r\n O=ICIT\r\n S=IN\r\n C=US\r\n CN=MeshCommander Root CA\r\n Name Hash(sha1): e6773dcb281d379b6b0a2b5337f57bab814031b9\r\n Name Hash(md5): 7b92aadae2c55fc114b9cf2a27f55b9a\r\nSubject:\r\n O=ICIT\r\n S=IN\r\n C=US\r\n CN=muse.homenet.local\r\n Name Hash(sha1): 8b860183a274ed79ca3edfcb2bede31a3857aa0d\r\n Name Hash(md5): 2a6a59ff610b774414ba5d27bf19fed0\r\nCert Serial Number: 023615\r\n\r\ndwFlags = CA_VERIFY_FLAGS_ALLOW_UNTRUSTED_ROOT (0x1)\r\ndwFlags = CA_VERIFY_FLAGS_IGNORE_OFFLINE (0x2)\r\ndwFlags = CA_VERIFY_FLAGS_FULL_CHAIN_REVOCATION (0x8)\r\ndwFlags = CA_VERIFY_FLAGS_CONSOLE_TRACE (0x20000000)\r\ndwFlags = CA_VERIFY_FLAGS_DUMP_CHAIN (0x40000000)\r\nChainFlags = CERT_CHAIN_REVOCATION_CHECK_CHAIN (0x20000000)\r\nHCCE_LOCAL_MACHINE\r\nCERT_CHAIN_POLICY_BASE\r\n-------- CERT_CHAIN_CONTEXT --------\r\nChainContext.dwInfoStatus = CERT_TRUST_HAS_PREFERRED_ISSUER (0x100)\r\nChainContext.dwErrorStatus = CERT_TRUST_REVOCATION_STATUS_UNKNOWN (0x40)\r\n\r\nSimpleChain.dwInfoStatus = CERT_TRUST_HAS_PREFERRED_ISSUER (0x100)\r\nSimpleChain.dwErrorStatus = CERT_TRUST_REVOCATION_STATUS_UNKNOWN (0x40)\r\n\r\nCertContext[0][0]: dwInfoStatus=104 dwErrorStatus=40\r\n Issuer: O=ICIT, S=IN, C=US, CN=MeshCommander Root CA\r\n NotBefore: 1/1/2018 1:00 AM\r\n NotAfter: 12/31/2049 1:00 AM\r\n Subject: O=ICIT, S=IN, C=US, CN=muse.homenet.local\r\n Serial: 023615\r\n Cert: 90f01f5b7f0eaa083461992a87274b03d8af38e2\r\n Element.dwInfoStatus = CERT_TRUST_HAS_NAME_MATCH_ISSUER (0x4)\r\n Element.dwInfoStatus = CERT_TRUST_HAS_PREFERRED_ISSUER (0x100)\r\n Element.dwErrorStatus = CERT_TRUST_REVOCATION_STATUS_UNKNOWN (0x40)\r\n ---------------- Certificate AIA ----------------\r\n No URLs \"None\" Time: 0 (null)\r\n ---------------- Certificate CDP ----------------\r\n No URLs \"None\" Time: 0 (null)\r\n ---------------- Certificate OCSP ----------------\r\n No URLs \"None\" Time: 0 (null)\r\n --------------------------------\r\n Application[0] = 1.3.6.1.5.5.7.3.1 Server Authentication\r\n\r\nCertContext[0][1]: dwInfoStatus=10c dwErrorStatus=0\r\n Issuer: O=ICIT, S=IN, C=US, CN=MeshCommander Root CA\r\n NotBefore: 1/1/2018 1:00 AM\r\n NotAfter: 12/31/2049 1:00 AM\r\n Subject: O=ICIT, S=IN, C=US, CN=MeshCommander Root CA\r\n Serial: 065494\r\n Cert: 47c7ee6ffcf018ecd493631b7909cbd61cc8030d\r\n Element.dwInfoStatus = CERT_TRUST_HAS_NAME_MATCH_ISSUER (0x4)\r\n Element.dwInfoStatus = CERT_TRUST_IS_SELF_SIGNED (0x8)\r\n Element.dwInfoStatus = CERT_TRUST_HAS_PREFERRED_ISSUER (0x100)\r\n ---------------- Certificate AIA ----------------\r\n No URLs \"None\" Time: 0 (null)\r\n ---------------- Certificate CDP ----------------\r\n No URLs \"None\" Time: 0 (null)\r\n ---------------- Certificate OCSP ----------------\r\n No URLs \"None\" Time: 0 (null)\r\n --------------------------------\r\n\r\nExclude leaf cert:\r\n Chain: 90f01f5b7f0eaa083461992a87274b03d8af38e2\r\nFull chain:\r\n Chain: 3bf2b959269132595796685978af13f681842665\r\n------------------------------------\r\nVerified Issuance Policies: None\r\nVerified Application Policies:\r\n 1.3.6.1.5.5.7.3.1 Server Authentication\r\nCert is an End Entity certificate\r\nCannot check leaf certificate revocation status\r\nCertUtil: -verify command completed successfully.\r\n"}
{"level":"debug","message":"TLS cert subject CN matches target hostname (muse.homenet.local)? false"}
{"level":"debug","message":"TLS cert DNS Name matches target hostname? false"}
{"level":"verbose","message":"TLS certificate verification results: false"}
For some reason IMC is determining that the hostname does not match the certificate Subject CN, when in fact it does. See the false results in the log messages above.
Looking for some insight on why this is happening and what to try next.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Side note: Do posts here need to be approved by a moderator before appearing on the site? I didn't think so as usually when I post something it appears right away. However I posted a reply to this thread earlier that is not showing up.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, ICIT,
The new posts are instantly included on the website, no moderator approval is necessary; maybe the tool had an issue.
Regarding the IMC version installed; did you uncheck the SHA1 option while doing the update?
Regards,
Miguel C.
Intel Customer Support Technician
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hmm, ok. It looks like my post was lost. I'll work on recreating. Sigh.
When you say "did you uncheck the SHA1 option while doing the update" I'm not sure what you're referring to. I simply ran the IMCInstaller-2.4.0.msi installer, I don't think there was any option regarding SHA1 during that process. Can you elaborate?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, ICIT,
I was referring to your comment on 07-12-2023 at 06:59 PM.
I uninstalled it per the IMC user guide, which is basically just using the Control Panel > Programs > Uninstall a Program function in Windows. I then deleted the C:\Program Files (x86)\Intel\Intel Manageability Commander directory and re-ran the IMCInstaller-2.4.0.msi installer. Note that I checked the SHA1 hash to confirm that my installer wasn't modified/corrupted.
Regards,
Miguel C.
Intel Customer Support Technician
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I just meant that I verified the SHA1 hash of the file I downloaded matched was is shown on the download page
Also, I see that my missing post finally showed up (twice).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, ICIT,
I hope this email finds you well.
The Certificate issue is known; self-Certificates are not supported anymore. In section 4 - Known Issues of the Intel® Manageability Commander (Intel® MC) Release Notes further details are available.
It is necessary for a third-party Intel® AMT certificate chain.
Vendor Certificates to Support Intel® AMT, bottom of the page.
About the IMC version issue, I am working with the engineering department; I will make sure to provide an update in a few days.
Regards,
Miguel C.
Intel Customer Support Technician
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is not a self-signed certificate though. I created it using MeshCommander's built-in certificate authority. It is signed by a root CA certificate, also created in MeshCommander, that is trusted on the Windows system that IMC is running on.
There is a valid chain of trust so it should work.
As far as Intel AMT specific certificates, it's my understanding that those are needed only for initial provisioning when the AMT client is reaching out to the Setup and Configuration Application (SCA). That type of certificate must be installed on the SCA device, for example, when using Endpoint Management Assistant server.
I can't find any documentation stating that creating TLS connections to a client require a special certificate. Per the IMC documentation, the only requirement mentioned regarding certificates is that a certificate must be trusted on the Windows computer.
6 Certificate Checking
Intel MC automatically verifies that certificates, used in TLS, chain down to a root in the Windows Computer Account Trusted Root certificate store of the machine from which it is run. Additionally, the Intel MC will verify that the DNS name or Subject Name in the certificate matches the host name of the Intel AMT device. Just like in web browsers, the machine will automatically connect and display a lock indicating that the connection is secured via TLS. If the certificate cannot chain to a root in the certificate store, then Intel MC will reject the connection and display an appropriate error message.
Additionally, I looked at section 4 of the IMC release notes but there is nothing mentioned about certificates.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, ICIT,
I am working on both questions with the engineering department. An answer will be provided in a timely manner.
Regards,
Miguel C.
Intel Customer Support Technician
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks. In the meantime I tried a different approach by adding an AMT certificate via PowerShell, using OpenSSL to generate the certificate. I followed the procedure documented here:
Intel vPro Technology Module for Windows PowerShell Installation and User Guide.pdf
6.14 TLS Configuration Flow Using PowerShell Snippets
here:
Intel AMT Implementation and Reference Guide
and here:
GitHub - rgl/intel-amt-notes: notes about intel amt
I created a new root CA certificate in OpenSSL that is trusted on the Windows computer where IMC is running. The AMT certificate is signed by that root CA.
In the end no luck, I still get the TLS error when attempting to connect. Although I did notice the IMC debug log was lightly different
{"level":"debug","message":"TLS cert subject CN matches target hostname (muse.homenet.local)? true"}
{"level":"debug","message":"TLS cert DNS Name matches target hostname? false"}
{"level":"verbose","message":"TLS certificate verification results: false"}
It now shows that the cert subject CN matches the target hostname, whereas before it returned false. The DNS name match is still false, although I'm not certain if that's required to be true. There's nothing in the documentation that I can find that mentions anything about a DNS name needing to be in the TLS certificate other than the Subject CN.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We have the same issue with EMA provisioned machines with TLS relay.
We install the MeshRoot cert (to Machine\TrustedRoot) and Ema Mesh cert (Machine\Personal) and MeshCommander works with TLS enforced, but same TLS error in Intel Manageability Commander.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page