- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We are currently working an issue with our Meraki WiFi and our Windows 10 devices. We have windows configured with 802.11x machine certificate authentication. We have discovered an issue that causes the client to disconnect and reconnect based on a certain set of actions.
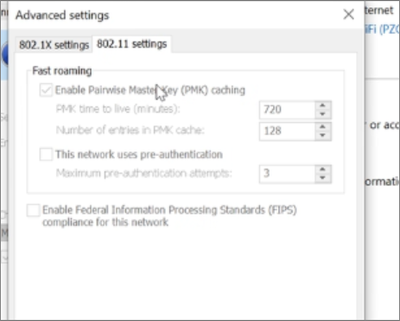
We have our clients configured with Fast roaming enabled. (PMK Caching and Preauthentication). When the client successfully connects to the ap, it will stay connected indefinitely. At the pre-defined interval for PMK caching (12 hours) it will seamlessly renew itself. We see an event on the ISE server backend ( successful auth) and a successful authentication in the meraki portal. Never disconnects.
If the client roams among AP's, the roam is flawless. The client never disconnects, is never forced to re-authenticate (not activity in the ISE logs and no authentication event in Meraki) only association or disassociations as expected.
However, if the client has been roaming, when the PMK cache expires (12 hours), the client fails to renew seamlessly. We can see in the event logs that is sends an EAP start command but the AP immediately de-authenticates the client. The client tries 3 more times to authenticate, fails and then resets the connection. Not such a big deal, except if this process occurs during a Teams or Zoom call, there is a network drop that is obvious to the end user.
We have worked with Meraki and Microsoft support, have seen the issue on Dell and Surface devices. Everyone is pointing to the Adapter drivers. We have tried every driver that Intel releases as soon a new one comes out.
Link Copied
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Jason_jm,
Thank you for posting on the Intel® communities.
In order to better assist you, please provide the following:
1. Run the Intel® System Support Utility (Intel® SSU) to gather more details about the system.
· Download the Intel® SSU and save the application on your computer: https://downloadcenter.intel.com/download/25293/Intel-System-Support-Utility-for-Windows-
· Open the application, check the "Everything" checkbox, and click "Scan" to see the system and device information. The Intel® SSU defaults to the "Summary View" on the output screen following the scan. Click the menu where it says "Summary" to change to "Detailed View".
· To save your scan, click Next and click Save.
Regards,
Deivid A.
Intel Customer Support Technician
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
and what do you want me to do with the results?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Jason_jm,
Once you have the report, you just need to attach it to your reply/post and we will proceed to check further information about the system.
The tool doe not collect personal information, just information about the hardware and software.
Best regards,
Deivid A.
Intel Customer Support Technician
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Unfortunately that is not correct. The tool pulls events from the windows event logs that include details about group policy. These events contain details and information about our active directory domain. I will work on cleaning it up.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Jason_jm,
Thank you for the information provided
I will proceed to check the issue internally and post back soon with more details.
Best regards,
Deivid A.
Intel Customer Support Technician
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Jason_jm,
We have some community members reporting a similar situation. Intel has started working directly with Cisco and Microsoft to understand where the root cause of the problem is.
- Make sure AP has the latest firmware available from AP OEM (Original Equipment Manufacturer).
- Make sure that Windows® 10 Wi-Fi Drivers for Intel® Wireless Adapters - Version: 21.60.2 or later is installed:
https://downloadcenter.intel.com/download/29258/Windows-10-Wi-Fi-Drivers-for-Intel-Wireless-Adapters
- One common factor that we have noticed is that some community members have the CCKM (Cisco Centralized Key Management) option enabled by default so try disabling it.
- Some other community members have reported that disabling the 802.11R (Fast transition feature) also fixes the problem for some of them.
In the meantime, we need you to also open a case directly with Microsoft to get all cases tracked.
Check download center once in a while for new drivers releases.
Best regards,
Deivid A.
Intel Customer Support Technician
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Deivid,
I'm in the Cisco Account team supporting this customer.
Can you provide some contacts at Cisco and Intel to follow up on this issue?
You can send me a direct message.
Thank you,
Manuel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks. We have several cases open with Cisco, Microsoft and Dell. Luckly we were able to reproduce it on a Surface Pro 7+ so MS is looking at it from a HW and SW perspective.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @Manuel_CISCO ,
I do appreciate your help on this matter, however, I will request privately some information from Jason_jm before we continue further.
@Jason_jm, I will appreciate it if you can help me with the information requested to the email address associated with your community profile.
Best regards,
Deivid A.
Intel Customer Support Technician
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Deivid,
Please provide the contacts at Cisco and Intel to follow up on this issue.
Thank you,
Manuel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Jason_jm,
In order to help you further, I will send you an email to the e-mail address associated with your community profile, requesting some information that will help us to continue with the research.
Best regards,
Deivid A.
Intel Customer Support Technician
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Jason,
I would like to exchange with you about your configuration you are using today on Meraki side and windows 10 Laptop.
We are experiencing many issues when users roam or don't move.
I would like to implement Fast Roaming. We use 802.1x authentication and computer certificate.
You can join me by mail guillaume.rouard@pwc.com.
Thank you in advance for your help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am going to have my network architect reach out to you. He has been working this issue since last year. We have finally stabilized our roaming.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If possible, I would also be interested in what solution was defined here.
Thx
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Pete
You can contact me by mail if you want exchange on this topic.
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Jason_jm, We are also experiencing the same issue with Intel NIC sending two PMK IDs causing Access point to sending the de-auth during fast roaming. What was the solution you implemented to this?
we are running win10 with latest drivers and 21H2 TCP IP Lib version and getting "EAPOL Invalid MIC" errors for most of the wireless clients doing 802.1x EAP-TLS Auth with 802.11r enabled.
There is a separate discussion going on Meraki community where in they said disabling "PMK Caching" option on windows client solves the problem.
Meraki Community Link: https://community.meraki.com/t5/Wireless-LAN/Wireless-Invalid-MIC-EAPoL-4-way-handshake-is-failling/m-p/194087
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
But the problem with disabling PMK Caching is that this breaks seamless roaming.
The issue is still there as far as I've been able to check. After talking to Cisco BU this is something due to Windows clients, where windows suddnely changes from using OKCC to legacy SKC and then the roaming is broken (as the PKMID been used by the client when turning into SKC is not accepted by the WLC to protect traffic encryption generated by OKC and shared by all APs in the same flexconnect group).
We are using Cisco WLAN infrastructure to latest code, and Cisco BU recommends to add an AP SP they have released for code 17.9.3 to ask for full authentication in case this happen.
This needs to be fixed by Microsoft but I wonder if they are doing anything to fix it or not, as this post is really old and it was happening then, and now.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We never full resolved this. We went back and enabled all the network drops and now our clients prefer a wired connection when docked at their workspaces.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi ,
I am the author of the referenced post on the Meraki community.
@JPavonM Were you able to get any KB from Microsoft to fix this issue ?
What is strange and I have a hard time explaining is that the issues seems to be worsen by upgrading my Meraki APs to a more recent code. But from what I can get , this is 100% a client issue , but downgrading the AP afterwards doesn't solve the issue , it only reduce the frequency of the issue happening per week.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page