- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I am trying to provision a Lenovo Thinkpad T420 and T430 devices via Intel AMT. With Intel AMT enabled, I can see that these devices listen on non-TLS port 16992. But the requirement is to provision these devices using TLS PKI mode via TLS port 16993.
I have tried to follow the instructions given at:
https://software.intel.com/en-us/blogs/2012/01/18/how-to-create-amt-certificates-using-the-amt-sdk-and-openssl
I created the powershell script with all the required details as mentioned in the above link. However, when I run the powershell script, I see the following error returned by these devices: "No route can be determined to reach the destination role defined by the WSAddressing To."
I have also verified that WinRM service is up and running on these devices as mentioned at https://software.intel.com/en-us/Intel%20-AMT-and-WS-Man-Tips
Using WMI tools I could see none of the CIM elements - AMT_PublicKeyManagementService, AMT_TLSProtocolEndpointCollection, AMT_TLSSettingData, AMT_SetupAndConfigurationService in any of the namespaces on these devices. In fact, I do not see any of WS-Management AMT classes mentioned at https://software.intel.com/sites/manageability/AMT_Implementation_and_Reference_Guide/WordDocuments/amtclasses.htm
On the other hand, the following CIM elements are visible in \\root\Intel_ME namespace after installing Intel Management Engine Interface Driver (which contains MeProv.dll)
AMT_EthernetPortSettings
AMT_ProvisioningCertificateHash
AMT_Service
AMT_SetupAuditRecord
ME_Event
ME_System
OOB_Service
Can anyone please suggest how should I go about configuring the TLS port to provision the Lenovo Thinkpad T420/430 devices via Intel AMT?
Thanks in advance,
Anand Navale.
Link Copied
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey Anand
The method you are referencing above is not going to configure the device into a TLS mode. The certificate being discussed is the Remote configuration certificate that allows the client to be remotely configured without purchasing a third party certificate. In this case the communication for AMT configuration is SSL and does not leave AMT in a TLS state.
As you indicate you are wanting AMT to listen on the TLS port of 16993, you will need to change how the configuration profile is created.
If you are using SCS or ACUWizard to create the profile the process is the same, open the profile editor and modify your current profile by:
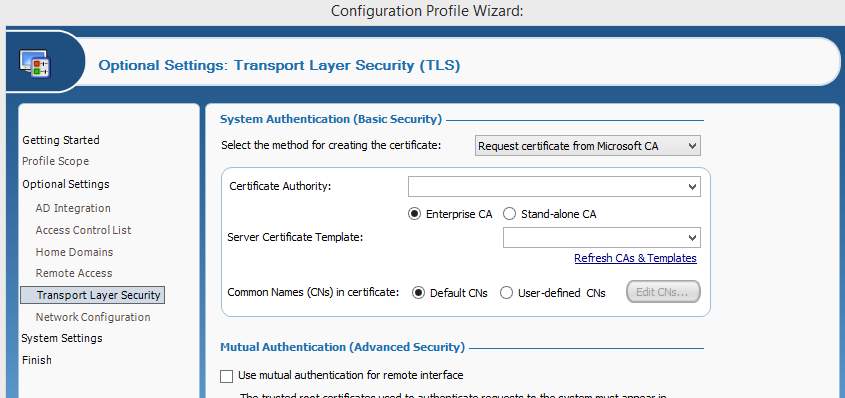
- Selecting the "Transport Layer Security (TLS)" option from within the "Optional Settings" menu item
- On the "Transport Layer Security" page you will need to specify the CA and template for the TLS certificate.
- Finish up the profile creation and perform your configuration process again using the new profile
Hope that Helps
Joe
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page