- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, I am confused while digging into the page swapping process. I have read the Intel SDM and the MEE paper. Here is my question.
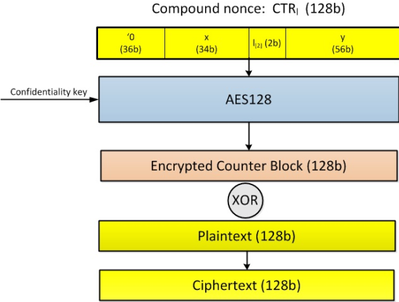
(1) The MEE paper says that when the data is moved from cache to the EPC, it is encrypted and integrity protected. The encryption scheme used is a tweaked AES Counter Mode, in which the cache line address (shown in the Figure below as x, and I am assuming the physical address here) is involved as the spatial coordinate, while the 56-bit counter (shown in the Figure below as y) is the temporal coordinates. As a result, I think the enclave data can only be decrypted successfully when it is loaded into the cache, if the data is stored in the same physical address (as it is stored previously into the memory from the cache).
(2) According to Intel SDM, the EWB instruction will encrypt the EPC page and copy the encrypted page along with some metadata (such as the page version number for replay protection, and the MAC for integrity protection) to untrusted memory. Then the ELDU/B instruction can decrypt the data from the untrusted memory and verify the version number as well as the MAC for freshness and integrity. If the verification passes, the data is copied back to the EPC.
My question is: whether the EPC page is copied back to the same physical address (as the physical address before the eviction)? If not, I think it may not be decrypted successfully when the data is loaded back to the cache, since the cache line address changes (see item (1) above).
Maybe, I am thinking it is possible, the EWB instruction will first decrypt the EPC page and get the plaintext enclave data, then encrypt the plaintext data, which is sent to the untrusted memory. When it is loaded from the untrusted memory to the EPC, the ELDU/B instruction will decrypt and get the plaintext enclave data, then encrypt it again using the new cache line address as part of the CTR. However, the SDM seems to inform that the EWB instruction only encrypts the EPC page (without decrypting it first).
Thank you for your time.
Wenhao
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for your response.
As I read through the Foreshadow paper, I think I have resolved the issue. The foreshadow paper mentions that the ELDU instruction will decrypt the page to get the plaintext data and put the data into L1 cache.
Best,
Wenhao
Link Copied
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Helllo yunfeng7854,
I will consult with my resources and respond on this thread as soon as I have an answer.
Sincerely,
Jesus G.
Intel Customer Support
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello yunfeng7854,
Your answer may be found in section 5.5 EPC Page Eviction of SGX Explained.
Sincerely,
Jesus G.
Intel Customer Support
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for your response.
As I read through the Foreshadow paper, I think I have resolved the issue. The foreshadow paper mentions that the ELDU instruction will decrypt the page to get the plaintext data and put the data into L1 cache.
Best,
Wenhao
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This thread has been marked as answered and Intel will no longer monitor this thread. If you want a response from Intel in a follow-up question, please open a new thread.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page