- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I have a question about how to check the legitimacy of an enclave application from the outside.
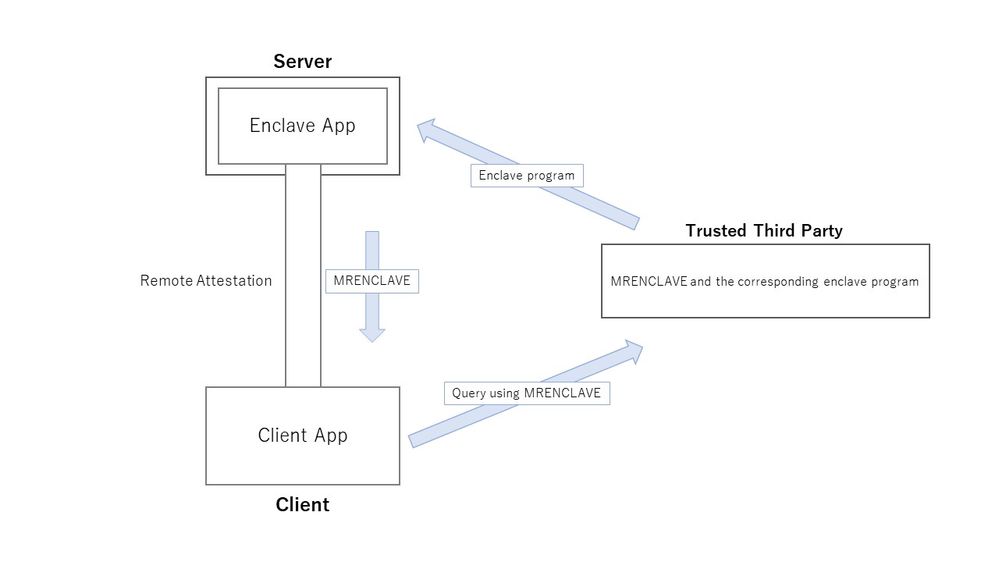
I envision the following scenario: the enclave application runs on a remote server, and the client verifies the legitimacy of the enclave program's application on the server before executing it.
By performing remote attestation, the MRENCLAVE of the enclave program on the server can be obtained, which allows the client side to know what program is running on the server. However, how can I link this MRENCLAVE to a legitimate program? I thought that a trusted third party could store MRENCLAVE and the corresponding program, to which the client could query to determine if the enclave program running on the server is legitimate. Therefore, I would like to have a trusted third party check the enclave program, etc. in advance to guarantee its validity, but I do not know how a trusted third party can calculate MRENCLAVE.
How can a trusted third party calculate the MRENCALVE corresponding to the enclave program? Or is there another way for the client to verify the legitimacy of the enclave program on the server?
Sincerely,
adukots
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi again adukots.
Unfortunately, the only way to get the MRENCLAVE of an enclave is to have the actual enclave binary. BTW, an enclave is simply a specially compiled library (.so in Linux, .dll in Windows) with the SIGSTRUCT added as already mentioned, so no need to reverse engineer anything, I don't think.
The way certain use cases (ie. joint muliti-party computation) do similar things (make sure source code compiles to a known MRSIGNER) is to have a reproducible build environment for the enclave. Then all involved parties could build and verify the MRSIGNER comes from the code they have analyzed.
But again, no way to get the MRSIGNER straight from source without building as the build process itself (compile/link options) all come into play to actually create the resulting enclave library/binary.
Regards.
Scott
Link Copied
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
When the enclave code/data pages are placed inside the EPC, the CPU calculates the enclave measurement and stores the 256-bit hash in MRENCLAVE. The contents of the CPU are compared against the enclave measurement in SIGSTRUCT, and the enclave will only be initialized if both match.
I've linked the part of the code here, where the measurement is compared.
If you have not already seen this Remote Attestation End-to-End sample, I recommend checking it out: https://www.intel.com/content/www/us/en/developer/articles/code-sample/software-guard-extensions-remote-attestation-end-to-end-example.html
Sincerely,
Sahira
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, Sahira,
Thank you for your reply.
When the enclave code/data pages are placed inside the EPC, the CPU calculates the enclave measurement and stores the 256-bit hash in MRENCLAVE. The contents of the CPU are compared against the enclave measurement in SIGSTRUCT, and the enclave will only be initialized if both match.
I've linked the part of the code here, where the measurement is compared.
I think your answer is a little off from what I had in mind, so let me restate the question.
The trusted third party has the enclave code and sends it to the server for execution on the server. If the server wants to receive data from the client at this time, the server and client would perform RA to confirm the validity of enclave before sending the data. However, MRENCLAVE obtained by the client at the time of this verification does not know which enclave program it corresponds to. Therefore, I considered it necessary to link MRENCLAVE and the enclave application, so that the client could query the trusted third party using MRENCLAVE and the trusted third party would return the enclave application corresponding to MRENCLAVE. However, I do not know how to link MRENCLAVE and enclave programs externally.
Is there a better way? Or is there another way to validate the enclave application on the server from the client, such as not using the trusted third party?
If you have not already seen this Remote Attestation End-to-End sample, I recommend checking it out: https://www.intel.com/content/www/us/en/developer/articles/code-sample/software-guard-extensions-remote-attestation-end-to-end-example.html
Yes, I have seen it. In this example, I think it is necessary for the client to know in advance MRENCLAVE corresponding to the enclave program. However, I don't think this sharing is easy since there is no way to verify if the provided MRENCLAVE is really the enclave program the client expects. Is there a solution to this? My apologies if I am wrong.
Best Regards,
adukots
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi adukots.
As Sahira mentioned, the MRENCLAVE that is calculated at build time is included in the signature structure (aka SIGSTRUCT) appended to the end of every SGX enclave binary. So, the trusted third party can read/use that directly, if need be.
You can also use the sgx_sign (open sourced) tool to dump the SIGSTRUCT (or build your own tool for the trusted third party) to see all the appended data, including the MRENCLAVE. This is tool that actually measures and appends the SIGSTRUCT to the enclave at build time. A sample command line to do this:
sgx_sign dump -dumpfile metadata.txt -cssfile sigstruct.hex -enclave libenclave.signed.so
You could even theoretically remove the SIGSTRUCT and measure the enclave at the trusted third server, again, using the open-sourced code contained in the sgx_sign tool. This exactly mirrors how the CPU would measure the enclave while loading before allowing it to launch.
Does this answer your question? If not, we will unfortunately need to have a bit more information/detail.
Regards.
Scott
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Scott,
I understood that I can send the SGX enclave binary to the trusted third party, where I can dump the SIGSTRUCT using sgx_sign and link the SGX enclave binary to the MRENCLAVE. However, in this way, the trusted third party cannot know how this binary will behave just by looking at it.
Is there any way to get the MRENCLAVE from uncompiled source code or other sources without building it? Or do I need to reverse engineer this SGX enclave binary and analyze how it works?
Best Regards,
adukots
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi again adukots.
Unfortunately, the only way to get the MRENCLAVE of an enclave is to have the actual enclave binary. BTW, an enclave is simply a specially compiled library (.so in Linux, .dll in Windows) with the SIGSTRUCT added as already mentioned, so no need to reverse engineer anything, I don't think.
The way certain use cases (ie. joint muliti-party computation) do similar things (make sure source code compiles to a known MRSIGNER) is to have a reproducible build environment for the enclave. Then all involved parties could build and verify the MRSIGNER comes from the code they have analyzed.
But again, no way to get the MRSIGNER straight from source without building as the build process itself (compile/link options) all come into play to actually create the resulting enclave library/binary.
Regards.
Scott
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Scott,
I was told that to get the MRENCLAVE of the enclave, I need the actual enclave binary, so I am planning to share this binary or prepare a similar environment on the trusted third party side and get the MRENCLAVE there.
Thank you very much for your response. It was very helpful.
Best regards,
adukots.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page