Hi,
I'm new here, was hoping to be able to get some support importing a wildcard certificate that worked on the previous BIOS version (02.01.0013).
We've reproduced the problem on two systems, after upgrading from 02.01.0013 to 02.01.0014.
BIOS UEFI update files:
https://www.intel.com/content/www/us/en/download/18911/intel-server-board-s2600wf-family-bios-and-firmware-update-package-for-uefi.html?wapkw=S2600WFT%20
Platforms are Intel R1208WFTYSR:
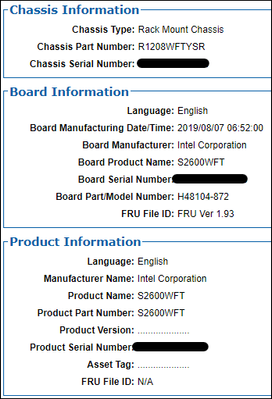
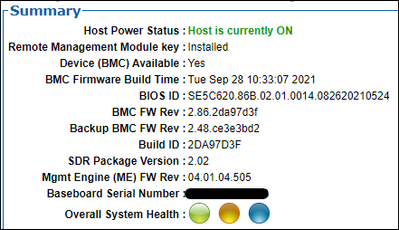
BMC version information:
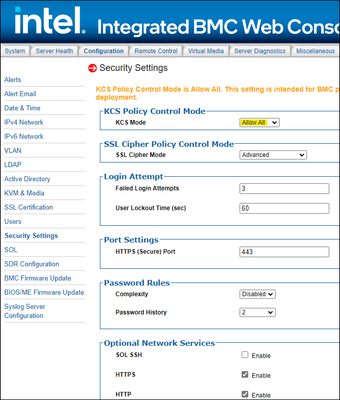
Security Settings:
Uploading SSL certificate files:
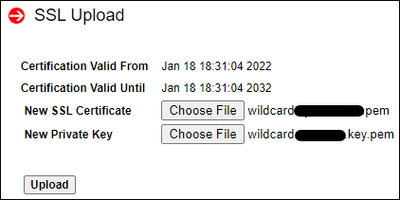
I confirm to replace the self generated one (BMC web interface was unavailable for approximately 5 minutes before appearing to have replaced the previously working certificate and key with a new self-generated one):
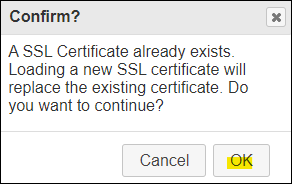
Resulting error:
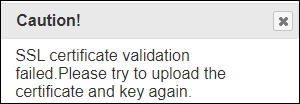
We have dumps via syscfg of the BIOS and BMC settings, should it be relevant.
Herewith information on the certificate:
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
f0:84:9c:f0:23:15:cd:b3:d7:dd:a2:28:70:a8:c0:b1
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=GB, ST=Greater Manchester, L=Salford, O=Sectigo Limited, CN=Sectigo RSA Domain Validation Secure Server CA
Validity
Not Before: Sep 24 00:00:00 2021 GMT
Not After : Sep 24 23:59:59 2022 GMT
Subject: CN=redacted.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public Key: (2048 bit)
Modulus (2048 bit):
<snip>
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Authority Key Identifier:
keyid:8D:8C:5E:C4:54:AD:8A:E1:77:E9:9B:F9:9B:05:E1:B8:01:8D:61:E1
X509v3 Subject Key Identifier:
90:FE:50:C3:E4:CC:3B:8D:D7:BB:2C:D8:90:F1:A3:7E:18:74:25:29
X509v3 Key Usage: critical
Digital Signature, Key Encipherment
X509v3 Basic Constraints: critical
CA:FALSE
X509v3 Extended Key Usage:
TLS Web Server Authentication, TLS Web Client Authentication
X509v3 Certificate Policies:
Policy: 1.3.6.1.4.1.6449.1.2.2.7
CPS: https://sectigo.com/CPS
Policy: 2.23.140.1.2.1
Authority Information Access:
CA Issuers - URI:http://crt.sectigo.com/SectigoRSADomainValidationSecureServerCA.crt
OCSP - URI:http://ocsp.sectigo.com
1.3.6.1.4.1.11129.2.4.2:
...k.i.w.F.U.u.. 0...i..}.,At..I.....p.mG...|..c .....H0F.!.... 6..xS.>..Sk/..I.Z..r.\.i.....!..]{V.Ls.'.>_.j...G_.{.)A)5.@.T...w.A...."FJ...:.B.^N1.....K.h..b......|..b......H0F.!..CR!..Ra.j....h...$i.....k.ib(...!..1..P.....X`..@M?D=.....sz;....U.u.)y...99!.Vs.c.w..W}.`
..M]&\%].....|..b......F0D. Ba\z7........|C..v.....ppl.....%. L...FL.........}.......T........
X509v3 Subject Alternative Name:
DNS:redacted.com, DNS:*.redacted2.com, DNS:*.*.redacted3.com, DNS:*.redacted.com
Signature Algorithm: sha256WithRSAEncryption
<snip>
|
PS: Trying to turn off HTTPS and only have HTTP enabled results in all web access being blocked. Be sure to set KCS to allow all to avoid bricking (technically locking yourself out) the BMC. If KCS it in allow all mode you can run 'ipmitool raw 0x30 0xb1 0x01 0x79 0x00' on a Linux host to enable HTTPS on LAN channel 3 (dedicated port).
Regards
David Herselman





