- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
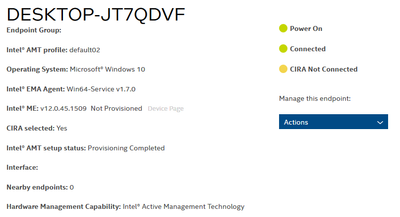
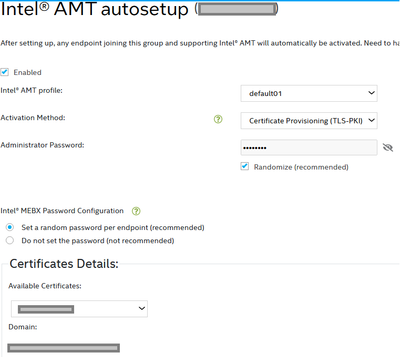
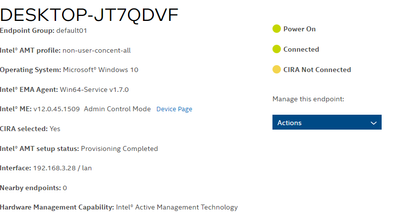
An Endpoint Group was created using TLS-PKI and EMAAgent was executed.
But the Intel ME is not provisioned, so the CIRA is not connected.
I can't find any logs even in the "Intel Management and Security Status" program in the Client.
Is there any way I can see the log to find out why?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello jic5760,
Thank you so much for your response.
We are glad to hear that the problem with CIRA has been fixed.
Please find your questions answered below:
1-Is the FQDN not changing in the Web Management UI a bug in EMA? Or is it not originally intended?
R/It is not a bug, as per our knowledge, it is intended that once you complete the configuration the only way to change the FQDN is to re-do the configuration from scratch, there isn’t really an instance where you need to change it unless there is a problem related to it.
2-In a multi-tenant environment, the FQDN of the server and the FQDN of certificates are inevitably different. How do these cases work?
R/You can create as many groups and as many tenants, as you like with the certificate you created, there is no need to create new certificates for every tenant although you can; however, it won’t be recommended.
Best regards,
Victor G.
Intel Technical Support Technician
Link Copied
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello jic5760,
Thank you for posting on the Intel® communities.
To continue with your request can you please provide the following information:
- Can you please provide the Intel® Active Management Technology (Intel® AMT) version been used on the endpoints?
- What version of Intel® Endpoint Management Assistant (Intel® EMA) is being used?
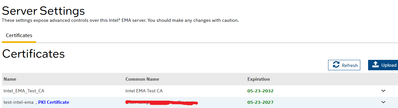
- When importing a provisioning certificate into the Settings page, is it showing as PKI Certificate?
Regards,
Victor G.
Intel Technical Support Technician
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, Victor.
1. v12.0.45
2. Intel EMA 1.7.0.0
3. Yes
CA certificates are also imported in Certificates.
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello jic5760,
Thank you so much for your response.
To continue with your request, please provide the following information:
1-How many systems in total do you have in this deployment, and how many are having this issue?
2-Can you please tell us a little bit more about the project that this issue is currently affecting?
3-Please provide a screenshot/picture of the certificates been used in EMA by logging yourself as a tenant and then going to the settings option in the EMA console.
4-There is an article we have when issues with CIRA are presented, please find it in the link below and let us know if it was helpful in any way.
How to Troubleshoot a Client Initiated Remote Access (CIRA) Connection in an Intel® Endpoint Management Assistant (Intel® EMA) Environment
https://www.intel.in/content/www/in/en/support/articles/000059019
Best regards,
Victor G.
Intel Technical Support Technician
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, Victor.
1. It's just one. This is an Intel NUC product. Provisioning worked normally with CCM, and I am trying to provision with ACM mode after Factory Reset.
2. Testing to apply Intel EMA.
3.
4.
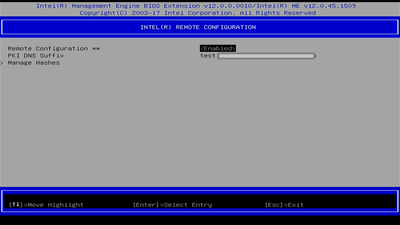
Because it is not provisioned, MEBx remains in the initial state, and even after the default password, admin login, the PKI DNS Suffix is Empty. (Note that I did a Factory Reset again after changing the password.)
And since provisioning has already been successful with CCM, there is no problem with the LMS Driver or the network.
The only expected problem is that the CA certificate is Self-Signed. Could this be the cause?
Doesn't EMAAgent store hash of the CA certificate in AMT? If not, is there a way to store a hash of the certificate from OS running?
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello jic5760,
Thank you for your response.
In this case, based on the information provided we believe the self-signed certificate is potentially the root cause of this issue. Please bear in mind that the recommended and validated certificates can be found in the following link.
For testing purposes, if you want to stay with the self-signed certificate due to the current environment you have what you can do is manually add your DNS PKI suffix directly into your MEBx BIOS and that should allow the endpoint to go from CCM to ACM (Please share pictures of MEBx in case you need guidance to do
this).
Regards,
Victor G.
Intel Technical Support Technician
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Victor,
Thanks for the reply.
Even though I manually set the DNS PKI Suffix, it doesn't work. Can I see the log somewhere?
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello jic5760,
Can you please confirm if you are getting an error message when you manually set the DNS PKI Suffix? If so can you please share it?
Best regards,
Sergio S.
Intel Customer Support Technician
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
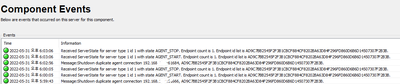
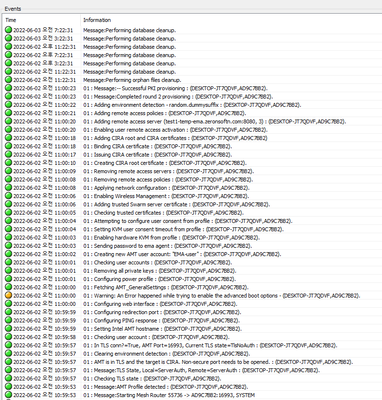
As shown in the screenshot above, there was no error in the CMOS screen.
After setting DNS Suffix in BIOS screen, EMAAgent was launched.
However, although the Agent is EMA registered, AMT is not provisioned with ACM mode.
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello jic5760,
In order to use your own certificate into the MEBx you want to follow these steps:
Entering a Root Certificate Hash Manually in the Intel AMT Firmware
Normally the certificate hashes are programmed in the Intel AMT system firmware by the manufacturer.
Alternatively, there is an option to enter the root certificate’s hash manually via the Intel MEBX. (The names and locations of menu options might vary slightly in different Intel AMT versions.)
To enter the certificate hash via the Intel MEBX:
1. Open the Root certificate and tab to Details. Keep the Root certificate thumbprint from the thumbprint field
for use in step 7.
2. Power on the Intel AMT system and press <Ctrl-P> during boot.
3. When the Intel MEBX menu is displayed, do a full unconfiguration (unprovision).
4. From the Intel MEBX menu, select Setup and Configuration > TLS PKI.
5. Select Manage Certificate Hashes.
6. Press <Insert> and enter a name for the hash
7. Enter the Root certificate thumbprint from step 1.
8. Answer Yes to the question about activating the hash.
9. Exit the Intel MEBX and reboot the Intel AMT system.
This needs to be done on every system MEBx prior to the provisioning attempt (executing the EMA agent)
Regards
Jose A.
Intel Customer Support Technician
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, Jose A.
Thank you for your reply.
Provisioning is completed normally by adding the certificate hash.
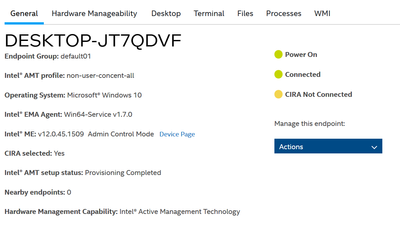
However, CIRA is still not connected.
Interestingly, it is connected to port 8080, so the log is written to the SwarmServer.
Thank you.
Lee.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
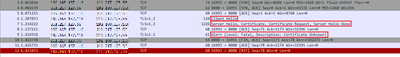
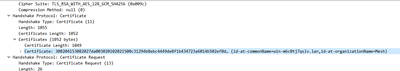
Hello,
I've captured packets and I'm having SSL issues.
The server's default certificate is delivered, not the Tenant PKI Certificate in the ServerHello packet. Perhaps this is the problem:
What could be wrong?
Thank you.
Lee.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello jic5760,
Thank you for posting on the Intel® communities.
Please let me review this information internally, and kindly wait for an update.
Once we have more information to share we will post it on this thread.
Regards,
Victor G.
Intel Technical Support Technician
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello jic5760,
Thank you so much for your patience.
After analyzing your situation on our end, we still believe the self-sign certificate is the root cause of the issue; therefore, please proceed with the steps below and let us know your outcome.
Steps
1-Un-provision the machine from the EMA web GUI, to do this once you have the GUI open go to the part that says take actions and then choose the option to un-provision.
2-Go to the endpoint and enter into MEBx and choose the option to un-provision found there.
3-Once the previously requested un-provisioning steps have been completed, please proceed to follow the steps below to create a new self-sign certificate.
How to Create a Self-Certificate Hash for Intel® Active Management Technology (Intel® AMT) Version 14 or Higher
https://www.intel.com/content/www/us/en/support/articles/000059996/software.html
4-Once you complete the self-sign certificate, proceed to uninstall the old EMA agent files, if you still have the old files in the machine you can use them to uninstall the files, you just need to run the ones you have in the machine and choose the option to uninstall, once that part is done you can proceed to create the new ones with the new certificate you just created.
5- Proceed to restart the endpoint and then go into MEBx and enter your PKI DNS suffix
Note: Please make sure that both the certificate that you create and the PKI certificate are named after the domain to which the EMA server belongs.
In case you have any doubts don’t hesitate to let us know.
For documentation purposes please provide the following report from the NUC:
Intel® System Support Utility (Intel® SSU)
Download link: https://downloadcenter.intel.com/download/25293/Intel-System-Support-Utility-for-Windows-
- Open the application and click on "Scan" to see the system and device information
- By default, Intel® SSU will take you to the "Summary View".
- Click on the menu where it says "Summary" to change to "Detailed View".
- To save your scan, click on "Next", then "Save".
Best regards,
Victor G.
Intel Technical Support Technician
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
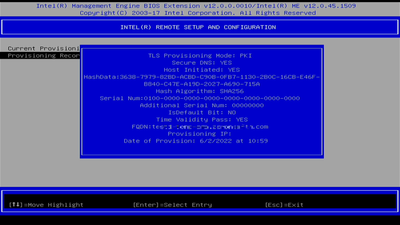
안녕하세요, 빅터 G.
친절한 답변 감사합니다.
알려주신 방법을 따랐습니다.
따라서 USBFile 도구를 통해 CA 인증서 sha256 해시(sha1 대신)를 성공적으로 등록했습니다.
> $me = new-Object 'Intel.Management.Mei.MeDevice'
> $me.Discover()
> $me.ACtiveHashes | findstr 3638
3638797982BDACBDC90B0FB711302B0C16CBE46FB840C47EA19D2027A690715A
그러나 여전히 CIRA는 SSL Alert 패킷과 연결되지 않습니다.
SSU 보고서도 첨부됩니다.
고맙습니다.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello jic5760,
Thank you for your response.
We appreciate the details you sent, to continue with your assistance can you please provide the log found in the following location: c:\Program Files (x86)\Intel\Platform Manager>\PatformManagerServer.log
In case you are not able to find the log you can watch it in real-time by accessing the Intel EMA platform manager. The steps to access it are down below, you can either copy the entries or send some screenshots of the ones that register errors.:
1-By default the tool is installed when the Intel EMA server is installed; therefore, you can look for it by using your Windows search bar directly in the machine that has the EMA server installed. Proceed to type Intel EMA platform manager and the app should appear.
2- Once you open it up click where it says connect server then enter your FQDN: port(8000) in the Platform manager server identified: port section. Then proceed with filling the section called Intel EMA web server identifier where you will need to enter only your FQDN, after that, you can leave the client auth certificate field with None, and proceed to hit okay.
3-A pop-up window should be open where you need to enter the username and password global administrator credentials, once you are logged in go to the tab that says EMA manageability server then go to the tab called events this one saves all the events in real-time.
Regards,
Victor G.
Intel Technical Support Technician
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, Victor G.
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello jic5760,
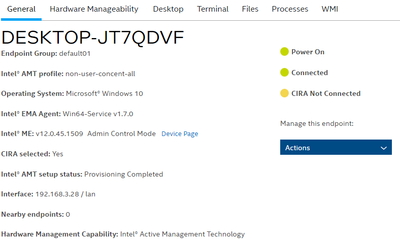
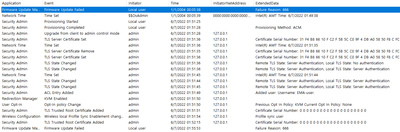
Thank you for sharing the logs, can you please send us an screenshot where it says CIRA is not connected?
We also are going to check the logs and will let you know our findings.
Best regards,
Sergio S.
Intel Customer Support Technician
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello jic5760
Thank you so much for your response.
We were able analyze the logs but the entries in them were kind old; therefore, please proceed to follow the steps below in order to get for us the most current entries live from the EMA platform manager.
Steps
1-Go to the server and open the EMA platform manager, once open move to the endpoint.
2-On the endpoint open the EMA web portal and choose the option that says stop managing endpoint.
3-Once the previous step is complete open the services app in the endpoint and locate the service for EMA, once located proceed to right click on it and choose the option to restart, once the service is restarting move immediately to the EMA server.
4-On the EMA server take a look at the EMA platform manager section where the entries will begin to be registered, please take a video or a screenshot of the entries that will start appearing. You can also just provide the most updated log found in the following location: c:\Program Files (x86)\Intel\Platform Manager>\PatformManagerServer.log
Best regards,
Victor G.
Intel Technical Support Technician
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, Victor G.
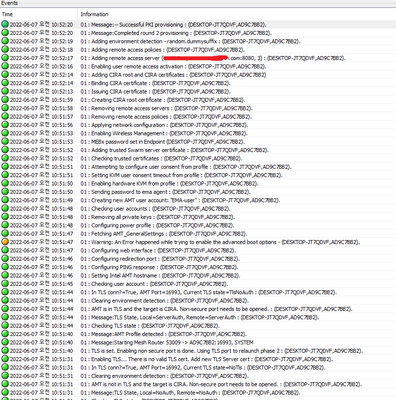
I unprovisioned and captured all the logs right before running EMAAgent again.
(`tail -n 0 -f PlatformManagerServer.log EMALogs/*.txt` in C:/Program Files (x86)/Intel/Platform Manager)
Attached as a file.
Client:
Thank you.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page