- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The Intel official remote attestation sample code, e.g. https://www.intel.com/content/www/us/en/developer/articles/code-sample/software-guard-extensions-remote-attestation-end-to-end-example.html, JMolding describe a model that encalve runs in client and server provides secret data, as the below picture shows.
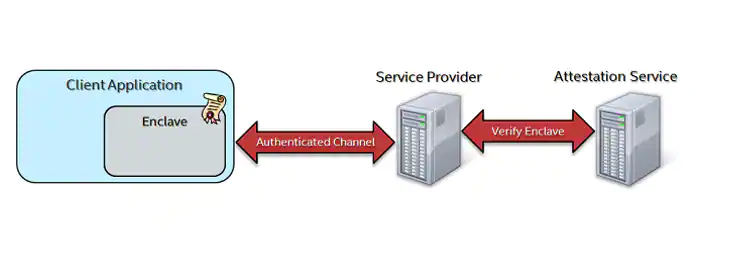
The Service Provider's public key should be hardcoded into the enclave. This, combined with enclave signing, ensures that the key cannot be changed by end users so that the enclave can only communicate with the intended remote service.
This fits intel's remote attestation model, but not mine. Because in my model, there are many client(secret data provider), and it's difficult to get the client's public key safely.
So, Is there a method to use intel sgx sdk in this model?
Link Copied
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Aqqibbjamshed839
Thank you for posting on the Intel️® communities. Please share with us more information on your current setup (components) and we will continue to investigate this request.
Regards,
David G
Intel Customer Support Technician
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Were you able to check the previous post?
Let us know if you still need assistance.
Best regards,
David G.
Intel Customer Support Technician
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We have not heard back from you, so we will close this thread. If you need any additional information, please submit a new question as this thread will no longer be monitored.
Best regards,
David G.
Intel Customer Support Technician
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm working on a research project that implements enclaves that, upon start, contact a key distribution/rotation server. This server holds all the private/public/symmetric keys needed and distributes them in a secure manner.
If you don't want to hardcore the RA Server's pubkey in your enclave, then use the untrusted part of your app to contact a server that all will provide the key for you. A way to secure the transaction is the use of MRSGINER as the identify of the enclave.
To sum up, the workflow could be the following:
- APP, UNTRUSTED: contact key server, fetch RA server's pubkey
- APP, UNTRUSTED: create the enclave, provision it with the pubkey
- APP, TRUSTED: complete the attestation process
- and so on.
But to be clear: be aware that the attestation's goal is twofold. The first is to attest an enclave, the second (which may interest you) is to establish a secure communication channel using the session key generated during the RA's DHKE. This is your secure way to exchange info between the RA server and the enclave.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page